The street finds its own uses for things.
—William Gibson, Burning Chrome
Imagine, if you will, a device you strap onto your lower arm. This device has a bunch of embedded myoelectric sensors that respond to hand movements, and accelerometers that track arm movements. Yoked to these is a Bluetooth transmitter that relays a stream of data about your hand position and arm motion to a computer or smartphone. Sound exciting?
Meet the Myo, a gadget in search of a purpose.

It’s a neat, if pricey, device still in search of a killer app. It comes with a PowerPoint plugin that lets you flip through slides by waving your arm in the air. There’s an interface for Skyrim, though it’s a bit laggy and you can’t play for long before your arm gets tired. There’s also a bit of software that lets you control a small drone with arm gestures, though with less precision than a conventional remote control. It’s very much a “build first, look for a function later” gadget, reminiscent of many tech innovations from the age of the dot-com bubble.
In most industries, the “build it and they will come” approach to project engineering is looked at with less and less favor these days. I am a long-time mad scientist with a particular flair for designing and building all manner of high-tech sex toys, though, so to me “build it and they will come” is what gets me out of bed in the morning.
As soon as I saw a demo of the Myo, my mind instantly went to sex. Controlling a device remotely by gesture and motion? What could possibly be more fitting in a sex toy? (In fairness, I did once, many years ago, build an Internet-controlled sex toy called the Symphony—a name that might perhaps be more appropriate for a device that you can operate by waving your arms. Dance, my puppets! Dance!)
So imagine my surprise when I Tweeted that this would make a cool controller for a sex toy and shortly thereafter one showed up on my doorstep, courtesy of AV Flox over at Slantist.
Electronically, the Myo is a Bluetooth LE radio, a set of myoelectric sensors, a suite of accelerometers, and a low-power processor core running proprietary firmware. Information from the myoelectric sensors is interpreted and translated into a set of posture information. This information is combined with data from the accelerometer and transmitted as a series of gestures and motions.
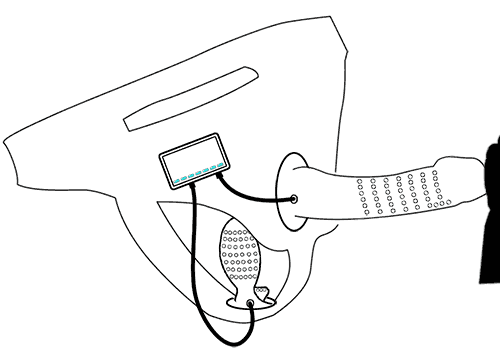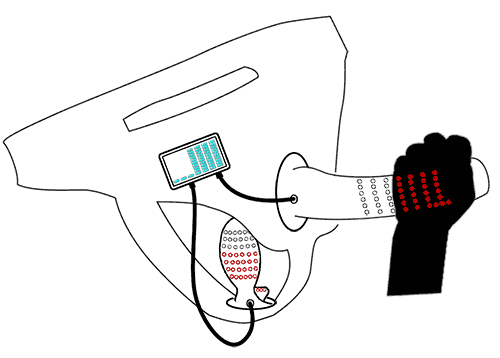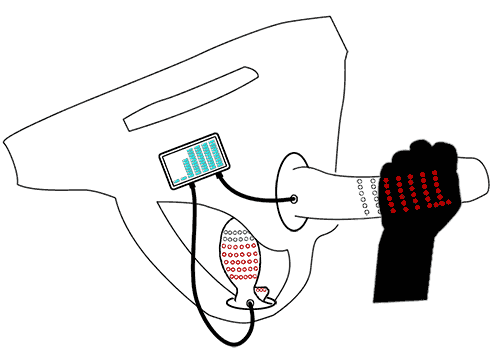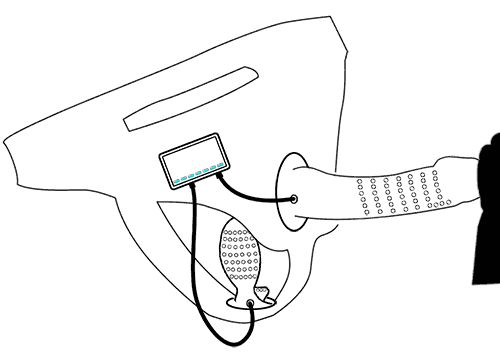
Conceptually, it looks a bit like this:
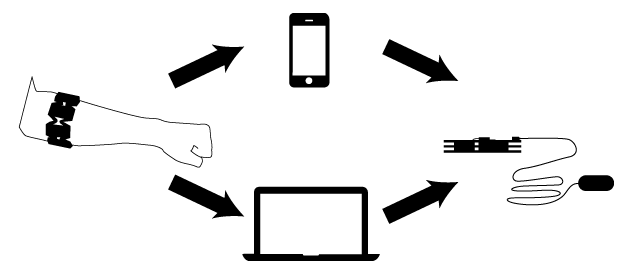
The Myo communicates with a laptop or smartphone. The laptop or smartphone interprets the messages from the Myo, then sends appropriate commands to an Arduino with a Bluetooth board connected, instructing it to to run (or stop) a vibrator attached to the motor driver.
The Arduino is a small single-board computer that was designed to do easy experimenting with programmable devices. Think of something like a Raspberry Pi, only far simpler and without an operating system. You can get many additional boards for the Arduino to do all sorts of things—Bluetooth, WiFi, networking, sensors, motor drivers, and other boards exist. The Arduino and its add-on boards are designed to be stacked on top of one another, to make project development easy.
The laptop or smartphone is necessary because of Bluetooth’s design. Bluetooth is a computer-to-peripheral technology. A Bluetooth network uses a master/slave topology, which means a Bluetooth peripheral can’t communicate directly with another Bluetooth peripheral—a “master” device like a laptop or smartphone is needed as an intermediary. When I first started working on a Myo-controlled sex toy, I did the development on a Macbook Pro laptop.
The Hardware
For the first-generation version of the gesture-controlled sex toy, I opted to use an Arduino Uno with a Red Bear Bluetooth shield and one of Kyle Machulis’ Pen15 vibrator controller boards, largely by virtue of the fact that I already happened to have all of them sitting on my workbench.
The Arduino is a small electronics board, roughly the size of an index card, that’s easy to program and capable of talking to all sorts of peripheral hardware. As a controller for a sex toy, it’s a bit large and clunky. Combined with a Bluetooth board and a motor control board, the whole ensemble is about as big as a pack of cigarettes; not exactly discreet. There are several much smaller development boards available, and a later version of this project will probably be about the size of a quarter.
The Arduino, Bluetooth board, and motor controller, all stacked atop one another, look like this:
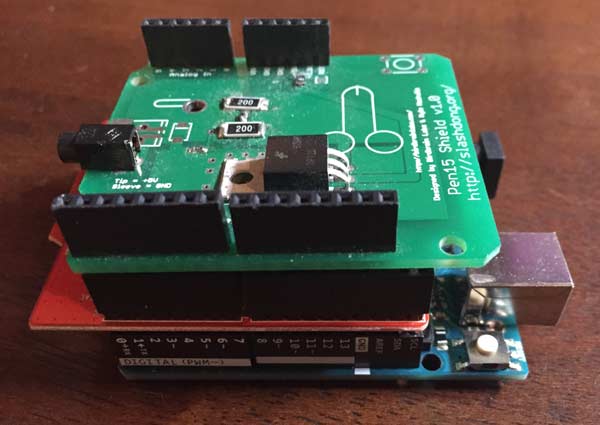
The blue board on the bottom is the Arduino itself, and contains the processor, power supply, and USB interface for programming. The red board in the middle is the Bluetooth board. The green board on top is the Pen15, an interface board designed specifically to run a sex toy from an Arduino. All together, this stack of boards cost about $40 or so.
The Software
Assembling the stack of components to make a Myo-controlled sex toy was the easy part. Writing the software turned out to be a bit more aggravating.
There are two parts to the software: a program running on the laptop (or smartphone, but for convenience I wrote the first version on my laptop), and a program running on the Arduino. The laptop software needed to pair with the Myo and the Arduino’s Bluetooth card, accept incoming data from the Myo, figure out how to translate those data into sex toy functions, and then send appropriate commands to the Arduino. The software on the Arduino needed to accept those commands and run the vibrator accordingly.
The Myo does a lot of on-board processing to figure out what hand gestures are being done, then sends the gesture data to the computer. It can recognize certain gestures, like making a fist, spreading your fingers apart, and tapping your thumb and forefinger together. It also sends information from the accelerometers, to report motion data.
For the first version, I wanted to keep things simple. I decided to look only at hand gestures, rather than arm motion. Making a fist, I decided, would turn the vibrator off; spreading my fingers would turn it on. (I opted not to control the speed of the vibrator, even though this is fairly straightforward for the Arduino to do, just to keep things simple.) This let me ignore accelerometer data and look only at hand gestures.
The Arduino software was relatively straightforward. The Arduino Bluetooth card comes with a programming library, which, much to my dismay, failed to work right out of the box. That’s surprisingly common in the world of Arduino development, where hardware and software is often designed by small groups of dedicated enthusiasts and may or may not work as expected the first time. An hour’s worth of Googling and some trial and error let me get the Arduino Bluetooth library working, and after that, things were a lot easier. I chose a command that would mean “vibrator on” and another that would mean “vibrator off,” and wrote a simple program that would poll the Bluetooth card looking for those commands and send the appropriate signal to the Pen15 board. All in all, the Arduino side of the equation took an evening to get sorted.
The computer/Myo side was a bit more complicated. The Myo I received was one of the first to ship, and the Myo’s software development kit was a mess when it was first released. (It’s still something of a mess now.) I had considerable difficulty pairing with both the Myo and the Arduino—something that wasn’t helped by the fact that Mac development is usually done in a language called Objective-C, and my experience with Objective-C is limited. It’s mostly like C++, mostly, but there are just enough differences to trip up anyone accustomed to C++.
I finally gave up on accessing the Myo directly and opted for a shortcut. The Myo comes with software that maps Myo gestures onto the keyboard, so I decided to make things even easier by going that route. I mapped an open-hand gesture to the letter ‘a’ on the keyboard and a fist to the letter ‘z,’ and decided to write the software so that it would send a “vibrator on” signal when it saw the letter ‘a’ and send a “vibrator off” signal when it saw the letter ‘z.’ I figured once I had that working, I could get more fancy and sort out accessing the Myo directly later.
It took a good bit of time to get even that part working. The software development kit for the Arduino Bluetooth card is, if anything, in an even more sorry state than the Myo SDK. It took a lot of hair-pulling to get the sample code to work properly, and it tended to break whenever I tried to modify it.
In the end, I did finally get it to work, after a fashion. It was (and still is) quite crude: it recognizes only two Myo gestures, which it translates into “run the vibrator at full speed” and “turn the vibrator off.” The software still has a maddening habit of losing touch with the Arduino occasionally, for no reason I can discern, but it works.
The test
I decided to try out the vibrator with one of my girlfriends who was visiting from the UK, where she lives. We had just finished a whirlwind three-week camping tour of ghost towns through the Pacific Northwest, a journey I am still chronicling.
We spent her last night in Portland at a hotel near the airport, and I thought, hey, this would be an awesome time to take the new toy for a spin, and maybe even get some video of the device in action. She thought that idea sounded splendid.
Unfortunately, the software had other ideas. As often happens, somewhere between being tested on my workbench and being tried in the real world, it decided to quit working. I debugged frantically while she lay naked in bed waiting. Eventually, she fell asleep, and the opportunity was lost.
Later testing would have to wait for a more favorable time. Eventually I was able to get it working again, but the moment to use it with her had passed.
The future
The current prototype gesture-controlled sex toy is quite primitive. Put together, it looks like this:

The hardware is still clunky. I plan to rebuild it using a DF Robot Bluno, which combines the Arduino and Bluetooth on a tiny board roughly the size of a quarter.

This should make it possible to create a discreet, miniaturized sex toy that can be worn in public. I have one of these sitting on my workbench, but haven’t had a chance to play with it.
Eventually, when I’ve made more progress on the strapon the wearer can feel and I have time to return to this project, I plan to refine the software, adding accelerometer control and allowing the vibrator to be controlled more precisely—perhaps by adding patterns to the vibration. (I have visions of doing a PowerPoint presentation at a business function while one of my partners sits in the audience wearing this device, as it responds to the same gestures I’m using to control the PowerPoint slides.)
Finally, I want to compile the control software for my iPhone, so I don’t have to lug around a laptop wherever I might want to use it. I can keep the iPhone in my pocket, where it silently listens to the Myo and sends signals to the sex toy.
The possibilities of remotely operated, Bluetooth-controlled sex toys that respond to wireless sensors, controllers, and other devices has a great deal of potential, especially if you’re a mad engineer like me. There’s rich territory here, just begging to be explored by intrepid adventurers. The early Myo prototypes are, I think, merely the tip of the proverbial iceberg. I can hardly wait to see what else is possible!



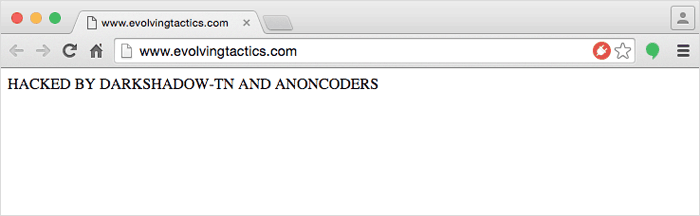
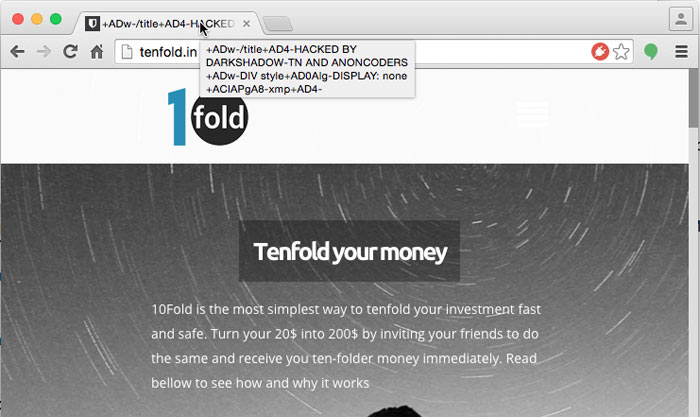

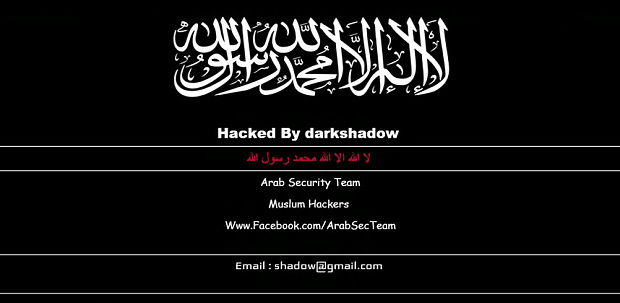


 It’s been a bad week for WordPress. If you’re a WordPress user, I highly recommend you check as soon as possible to ensure your site is updated, all your plugins are up to date, and your site is free of unexpected users and malicious combat.
It’s been a bad week for WordPress. If you’re a WordPress user, I highly recommend you check as soon as possible to ensure your site is updated, all your plugins are up to date, and your site is free of unexpected users and malicious combat.