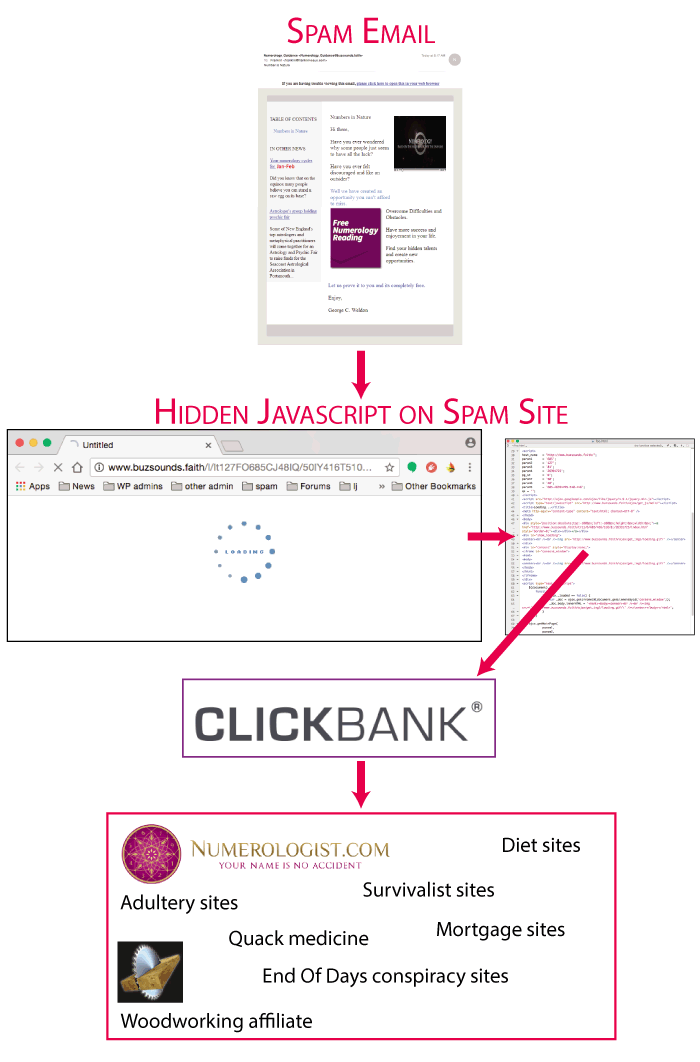
I have a rather extensive collection of Web sites, where I write about everything from photography to transhumanism to sex. As a result, I have rather a lot of domain names, which until recently I’ve registered with Namecheap, as they have in the past been cheap and reasonably reliable.
However, I have begun the painful and expensive process of moving off Namecheap, and I recommend others do the same. There are two interrelated reasons for this, the first having to do with poor support and training (Namecheap employees don’t appear to know the differnce between a domain and a subdomain, which is rather a serious problem when you’re in the business of domains) and the second having to do with support for spam and malware (largely on account of the first).
The story is long and complicated, but it begins many months ago with a spam email advertising life insurance, which was plugging a domain hosted on Namecheap Hosting.
Namecheap, in addition to being a domain registrar (well, technically a reseller for a registrar called Enom), is also a Web hosting company. If you’re a Web hosting company, sooner or later a spammer will host a Web site with you. How you react when you receive abuse reports will determine how popular you are with spammers. If you react quickly, spammers will avoid you. If you allow the site to remain up, spammers will talk, and soon other spammers will flock to you. If you continue to leave spam domains up, pretty soon spammers will start choking out your other customers.
Anyway, it happens. A spammer found Namecheap Hosting. I hadn’t seen much spam on Namecheap before, so I fired off an abuse report and that was the end of it.
Or so I thought. But then things took a turn for the strange.
A couple of days later, I received an email from Namecheap abuse saying “we aren’t hosting this domain, go complain to someone else.” Now, that happens from time to time as well; spammers will sometimes hop from one host to the next, so by the time a host receives a complaint, the spammer’s Web site has been moved and they’re not hosting it any more.
I looked at the domain. Still hosted on Namecheap. I wrote back saying “no, it’s definitely hosted by you guys; here’s the IP address, 162.255.119.254. That address is in your space.”
And got back a second email: “We’re not hosting this site.”
“Huh,” I thought, “that’s strange. Maybe the site is hosted on many IP addresses?” That’s another spam tactic, putting a Web site on a bunch of hosts and then changing the IP address constantly. But no, the site had only ever been hosted by Namecheap.
I replied and said “no, here’s the DNS entry, ere’s the history for the site, you’re definitely hosting it.” And got back yet another reply: “no we’re not.”
And then something even weirder happened.
I started getting tons of spam advertising domains pointing to Namecheap’s IP address space. Tons. Spam advertising life insurance, promoting Bitcoin schemes, advertising phony “cures” for diabetes. Spam pitching window replacement services, Amazon gift cards, Russian dating sites, and home refinancing.
And I’d seen this spam before. It was word-for-word and image-for-image identical to spam from well-known, infamous spam purveyors that had always, until now, advertised sites hosted in Russia, Columbia, and the Ukraine–places that tend to permit spam hosting.
I started getting multiple pieces of this spam a day. Then dozens. All of it advertising domains on Namecheap IP addresses.

 Left: Old spam advertising a site hosted in Eastern Europe. Right: Recent spam advertising a site on Namecheap.
Left: Old spam advertising a site hosted in Eastern Europe. Right: Recent spam advertising a site on Namecheap.I sent spam reports to Namecheap…and Namecheap’s abuse team kept sending responses saying “we aren’t hosting these sites.”
This is the point where I learned that Namecheap, a company that sells domain names, does not understand how a domain name works.
A typical domain name has three (or more) parts. The parts are separated by periods. Let’s look at an example:
www.morethantwo.com
Going from right to left: The last part is called a “top level domain,” or “TLD”. It’s things like “.com” or “.net” or a country-specific code like “.ca” (for Canadian sites). The UK uses “.co.uk” for various historical reasons.
The part before the TLD, in this case morethantwo, is the domain name.
The part at the very beginning, in this case www, is a subdomain. The subdomain “www” stands for “World Wide Web” and it’s the most common subdomain by far. But you can make a subdomain be anything you want. You could set up your Web site at “polyamory.morethantwo.com” or “groupsexisawesome.morethantwo.com” or anything else you like.
And here’s the important part:
You can put a subdomain on a completely different server, hosted by a completely different Web host.
For example, morethantwo.com is hosted by Incubus Web hosting. But if I wanted to, I could put “polyamory.morethantwo.com” on Dreamhost and “groupsexisawesome.morethantwo.com” on Softlayer–each subdomain can get its own IP address and its own Web server, if you want.
Now you might not know that, and you can be excused for not knowing that. It’s not necessary to understand how the Internet works in order to use it.
But Namecheap should know that. They sell domain names. This is what they do.
It’s okay if a person who owns a car doesn’t know that a car’s engine has more than one spark plug in it, but no professional mechanic should ever be ignorant of that simple fact. It’s okay if a person who uses the Web, or even a person who owns a Web site, doesn’t know that subdomains can be hosted on one IP address. It’s unforgivable that a domain registrar doesn’t know that.
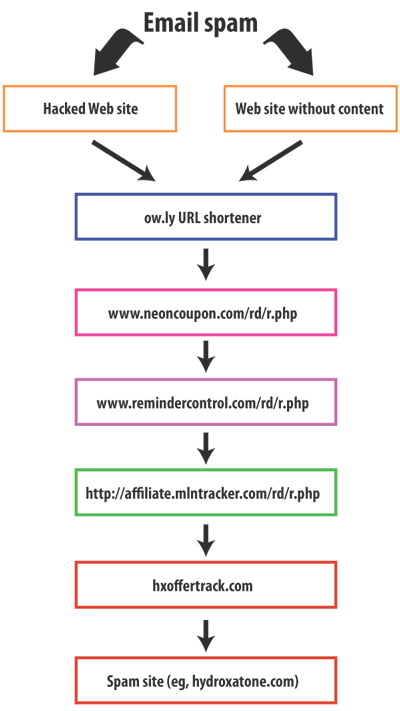
In this case, the spammer is using domain names that look like
view1.gnrlbshomes.us
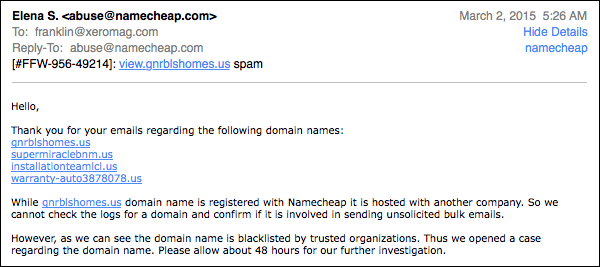
“view1” is a subdomain, hosted by Namecheap. The main domain,gnrlbshomes.us, is hosted elsewhere. Namecheap’s abuse team doesn’t know how that works. When they received the spam complaint, they didn’t look at view1.gnrlbshomes.us, they only looked at gnrlbshomes.us.
When I figured out what was happening, a light dawned. I fired off a reply explaining that view1.gnrlbshomes.us and gnrlbshomes.us were hosted at differnt IP addresses, and they were hosting the actual spamvertised URL, view1.gnrlbshomes.us.
Problem solved, right? They simply missed the subdomain, right? Wrong.
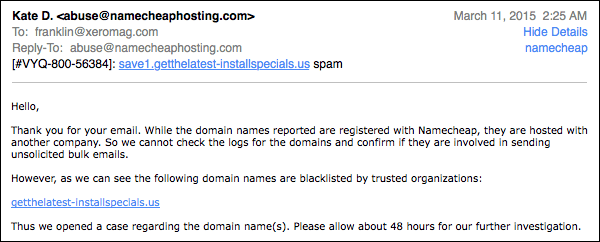
Elena, it seems, didn’t talk to Kate. Namecheap has a systemic problem. This isn’t someone not noticing the subdomain, this is someone not knowing how domains work.
And I got a lot of these emails, from all different people: “The domain ‘blah blah blah’ isn’t hosted by Namecheap.”
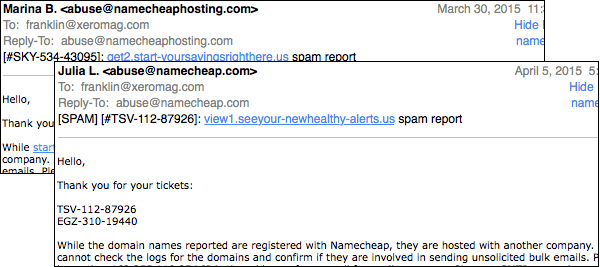
At this point, I was convinced the problem was incompetence…and a bizarre incompetence, an incompetence on the level of a professional auto mechanic not understanding that an engine has more than one spark plug.
But then, things took a turn for the even weirder.
I patiently replied to each of the emails, showing the IP address of the main domain and the subdomain, and that the subdomain was in fact on Namecheap IP space.
And then I started getting replies like this:
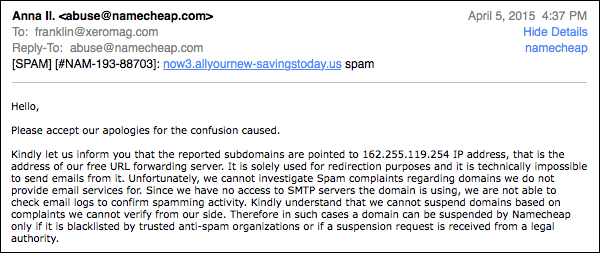
Essentially, what this says is “if you don’t actually send email from a Namecheap server, you’re welcome to spam a domain that lives in Namecheap space and we’re A-OK with that.”
Now, spammers almost never send emails from the same servers their Web sites live on. Usually, spammers send emails from home computers that are infected with viruses without their owner’s consent (a lot of computer viruses are written for profit; the virus authors infect computers with software that allows them to remotely control the computers, then sell lists of infected computers to spammers, who use the infected computers to send spam email.) Sometimes, the spam emails are sent from “bulletproof” spam mail servers in places like the Ukraine. But they almost never come from the same computer that’s hosting a site.
So Web hosting companies want to see a spam with full headers when you report spam, so they can verify that, yep, this is a spam email, and shut down the Web site that’s being spamvertised.
But not Namecheap. Namecheap will knowingly and willingly allow you to spam domains on their servers, provided the spam email doesn’t actually come from the same server.
I asked if their policy was to permit spam that doesn’t originate from the same server as the Web site, I received this reply:
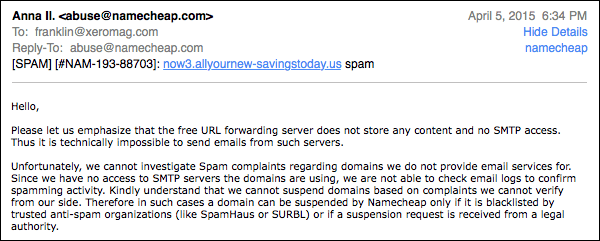
Which to me looks like a “yes.”
At the moment, I am currently receiving 11 spam emails a day advertising domains that resolve to Namecheap IP addresses. There are about half a dozen products being spamvertized; each day’s crop of spam messages are word for word and image for image identical to the previous day’s, but the domains are different. Clearly, the spammers feel they’ve found a good home in Namecheap.
So I took a look at that IP address, 162.255.119.254. It’s quite a mess.
Domains on 162.255.119.254 are all forwarded; that is, 162.255.119.254 is a pass-along to other IP addresses. If you want to put up a Web site and you don’t want anyone to know who’s really hosting it, you can put it there, and visitors will be invisibly passed along to its real home.
Now, can you guess what sort of thing that’s useful for?
If you said “spam and malware!” you’re absolutely right. A Virustotal analysis of 162.255.119.254 shows that it’s being used to spread a lot of bad stuff:
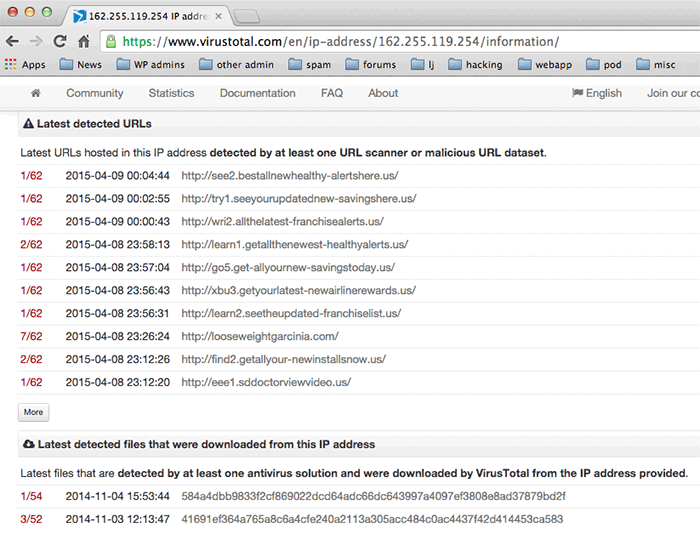
And it’s not just Virustotal. A Google search for 162.255.119.254 shows that it has a reputation as a bad neighborhood in a lot of places. It’s listed as a bad actor in the Cyberwarzone list:
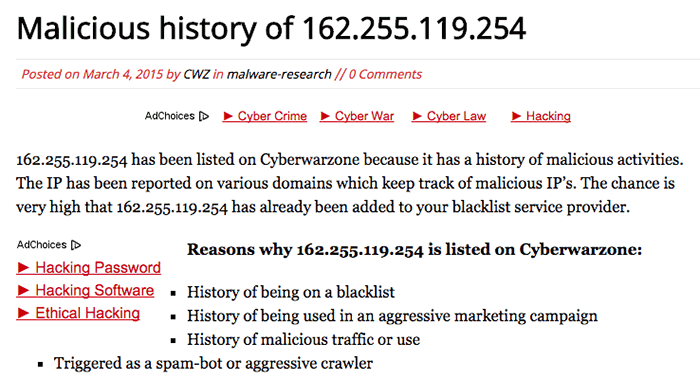
and as a virus distributor in the Herdprotect list:
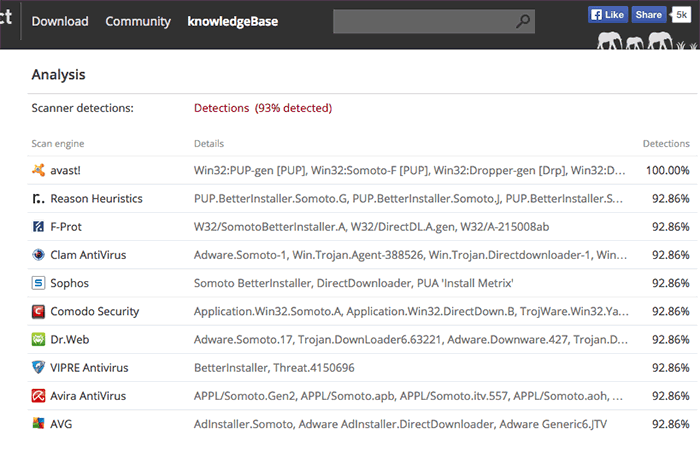
At this point, I got tired of making screenshots, but basically this Namecheap server has a bad reputation everywhere.
So whether through gross incompetence or active malice, Namecheap is running a server that’s a haven for spammers and malware distribution.
Which is why I’ve begun pulling my domain name registrations from them. I can not in good conscience spend money to support a company that’s such a menace to the Internet, and I spend about $500 a year in registrations.
Now, interestingly, I’m averaging about 11 spam emails a day advertising domains on Namecheap’s IP space, but I’m averaging 20 spam emails a day that are word for word identical to these but aren’t advertising a domain on Namecheap.
The ones that are advertising domains not on Namecheap are advertising domains hosted by a company called Rightside.co, a Web host I’m not familiar with.
As I mentioned before. Namecheap is a reseller for a registrar called Enom. And Rightside.co, well…
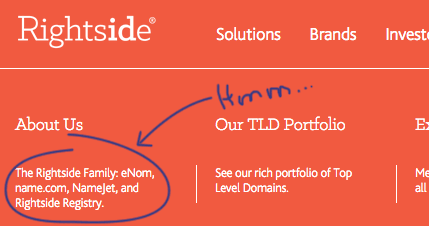
The fact that the same spammer is using Namecheap and Rightside, and they’re both front-ends for Enom, is interesting. Stay tuned!
Like this:
Like Loading...