I have a love/hate relationship with WordPress.
Actually, that’s not true. I like WordPress rather a lot, and I wish that more open-source projects had the finish, polish, and sophistication of WordPress. I own about a half-dozen Web sites that run it, and I’m overall very fond of it.
What I don’t like is the number of people who set up a WordPress install, then walk away from it and never install any updates or security patches. WordPress is a popular target for hackers, because it’s widely deployed and easy to find, and because so, so many people don’t keep on top of updates.
Which, frankly, baffles me. It’s incredibly easy to update–easier, in fact, than any open-source server software I’ve ever used. You log in to the admin area. It tells you “There is an update. Click here to install the update.” You click one button. Bang, that’s it! There literally is nothing else you have to do.
So, anyway, today I found yet another phony bank phish in my email. The phish pretends to be an HSBC Bank page, and it attempts to trick the gullible into handing out their bank account number and password. So far, so bog-standard.
*** WARNING *** WARNING *** WARNING ***
The URLs in this post are live at the time of this writing. They do not lead to malware sites, but they DO lead to phony bank phish sites.
The phish page in my email lives at
It’s a pretty bog-standard phish, a page living on a hacked server that collects personal financial information and then sends them off to the phishers via a php-to-email script.
The server that it lives on,
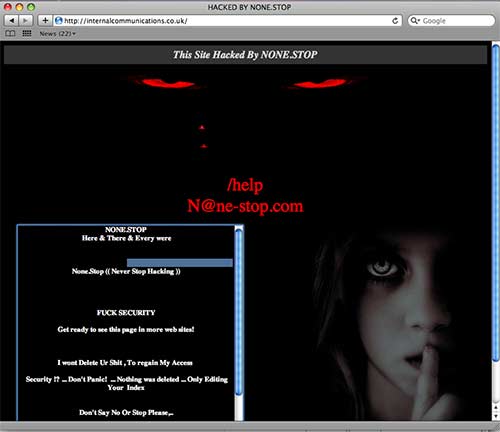
The site itself is completely defaced. The defacement left a hole big enough to drive a truck through, and the phishers put the phony bank page on the site after the person or group who defaced it hacked it and left it wide open. EDIT: The site defacer, who goes by the name “NONE-STOP,” is also a phisher who sells stolen credit card numbers, stolen bank account login information, and other stolen identity information. More at the end of this post.
The front page of the hacked site, as of the time of this writing, looks like this (click for larger):
I haven’t heard of NONE.STOP, whoever he/she/they are; as near as I can tell, there’s only one other site defacement (
Now is where it gets interesting, and where WordPress comes in.
Normally, when a site is defaced, the images that are used in the defacement are uploaded to the hacked server. Not in this case. In this case, the images used in the defacement are being remote loaded from another server.
A hacked WordPress install, that was set up a while ago, had a single test post added to it, and was abandoned.
Specifically, the images used in the defacement are being loaded from
and so on. The Web site
The site
$whois devriestree.com
Whois Server Version 2.0
Domain Name: DEVRIESTREE.COM
Registrar: GODADDY.COM, INC.
Whois Server: whois.godaddy.com
Referral URL: http://registrar.godaddy.com
Name Server: NS.NETVTECH.COM
Name Server: NS1.GEODNS.NET
Name Server: NS2.GEODNS.NET
Status: clientDeleteProhibited
Status: clientRenewProhibited
Status: clientTransferProhibited
Status: clientUpdateProhibited
Updated Date: 21-oct-2008
Creation Date: 19-oct-2005
Expiration Date: 19-oct-2010
Registrant:
NetVenture Technologies, Inc.
1490 S Military Trail
Suite 13E
West Palm Beach, Florida 33415
United States
Registered through: GoDaddy.com, Inc. (http://www.godaddy.com)
Domain Name: DEVRIESTREE.COM
Created on: 18-Oct-05
Expires on: 19-Oct-10
Last Updated on: 12-Jul-07
Administrative Contact:
DeVries, James j@netvtech.com
NetVenture Technologies, Inc.
1490 S Military Trail
Suite 13E
West Palm Beach, Florida 33415
United States
5613016666 Fax — 5618288035
Technical Contact:
DeVries, James j@netvtech.com
NetVenture Technologies, Inc.
1490 S Military Trail
Suite 13E
West Palm Beach, Florida 33415
United States
5613016666 Fax — 5618288035
Domain servers in listed order:
NS1.GEODNS.NET
NS2.GEODNS.NET
NS.NETVTECH.COM
The Web site at
Folks, seriously, update your WordPress installs. It’s automatic and effortless.
EDITED TO ADD:
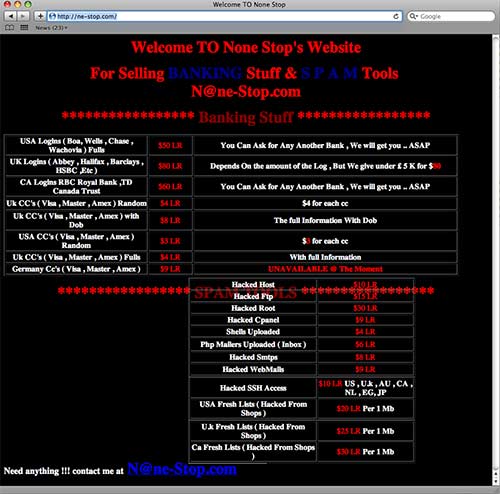
The person who defaced the Web site and who is storing his images on hacked WordPress sites has a Web site of his own, through which he sells stolen credit card numbers, phish kits, stolen bank account information, and so on. His Web site is at
hosted by Hurricane Electric.
$whois ne-stop.com
Whois Server Version 2.0
Domain Name: NE-STOP.COM
Registrar: REGISTER.COM, INC.
Whois Server: whois.register.com
Referral URL: http://www.register.com
Name Server: NS1.HE.NET
Name Server: NS2.HE.NET
Name Server: NS3.HE.NET
Status: clientTransferProhibited
Updated Date: 12-jan-2010
Creation Date: 11-jan-2010
Expiration Date: 11-jan-2011
>>> Last update of whois database: Mon, 18 Jan 2010 07:57:57 UTC <<< Registration Service Provided By: Hurricane Electric Internet Services Contact: hostmaster@he.net Visit: hurricanenames.net Domain name: ne-stop.com Registrant Contact: Ladde Weiong Ladde Weiong () Fax: 125 Club Garden Road Sheffield, S11 8BW GB Administrative Contact: Hurricane Electric Internet Services Hostmaster he.net (hostmaster@he.net) +1.5105804100 Fax: 760 Mission Court Fremont, CA 94539 US Technical Contact: Hurricane Electric Internet Services Hostmaster he.net (hostmaster@he.net) +1.5105804100 Fax: 760 Mission Court Fremont, CA 94539 US Status: Locked Name Servers: ns1.he.net ns2.he.net ns3.he.net Creation date: 11 Jan 2010 11:56:14 Expiration date: 11 Jan 2011 11:56:14 As of the time of this writing, the front page of the site looked like this (click for larger):

Oddly enough, I have a friend named Simon Wright who lives in Leicester, England. Is it worth asking him if he owns the hacked site, or not?
Oddly enough, I have a friend named Simon Wright who lives in Leicester, England. Is it worth asking him if he owns the hacked site, or not?
I actually don’t update my word press sites because (generally speaking) it breaks my word press plug-ins and results in an uncomfortable week of my ‘clients’ (primarily student organizations, setting up their sites is part of my job) yelling at me and hanging over my shoulder while I ‘fix something’ they can’t live without–that’s usually a result of a plug-in editor ending support just as wordpress releases yet another code-breaking patch. Even if I find another plug-in, or cobble one together that does the same thing myself, they’re never ‘quite’ the same and I get constant kvitching about it.
I’m a big plan of choosing a version, releasing in that version, and maintaining in that version. I do the same thing with java, visual studio, ruby, and python projects I’m working on too.
Hmm, really? I’ve not had any problems with WP plugins breaking; in fact,t he modern versions of WordPress can even automatically update plug-ins as well as the WordPress core files. It’s been effortless and hassle-free for me.
Are these sites using older plug-ins that are no longer maintained, or plug-ins designed for old WP versions?
I can understand why the WP maintainers release security patches only for the most current WP version; it takes considerable developer resources to continue to provide security updates for multiple codebases. Given the potential seriousness of a security breach, which could result in complete compromise of a server and/or uploading phishing pages or other illegal content to the server, I would tend to find that staying current with security patches outweighs potential pain with plug-ins, especially in light of the fact that recent, maintained plug-ins offer one-click updates themselves.
I actually don’t update my word press sites because (generally speaking) it breaks my word press plug-ins and results in an uncomfortable week of my ‘clients’ (primarily student organizations, setting up their sites is part of my job) yelling at me and hanging over my shoulder while I ‘fix something’ they can’t live without–that’s usually a result of a plug-in editor ending support just as wordpress releases yet another code-breaking patch. Even if I find another plug-in, or cobble one together that does the same thing myself, they’re never ‘quite’ the same and I get constant kvitching about it.
I’m a big plan of choosing a version, releasing in that version, and maintaining in that version. I do the same thing with java, visual studio, ruby, and python projects I’m working on too.
I’m wondering why we don’t hear more about site defacement which occurs simply to remind people that websites are vulnerable. (Or at least just some teen being an annoying 133+ h4xx0r.) I mean, surely deluded or crazy “good guys” still exist, right?
White-hat hackers probably don’t want to risk going to prison for doing good deeds, perhaps?
I’m wondering why we don’t hear more about site defacement which occurs simply to remind people that websites are vulnerable. (Or at least just some teen being an annoying 133+ h4xx0r.) I mean, surely deluded or crazy “good guys” still exist, right?
It certainly couldn’t hurt. I’d be surprised if it were the same person, but on the off chance it is, it might be worth pinging him.
It certainly couldn’t hurt. I’d be surprised if it were the same person, but on the off chance it is, it might be worth pinging him.
Hmm, really? I’ve not had any problems with WP plugins breaking; in fact,t he modern versions of WordPress can even automatically update plug-ins as well as the WordPress core files. It’s been effortless and hassle-free for me.
Are these sites using older plug-ins that are no longer maintained, or plug-ins designed for old WP versions?
I can understand why the WP maintainers release security patches only for the most current WP version; it takes considerable developer resources to continue to provide security updates for multiple codebases. Given the potential seriousness of a security breach, which could result in complete compromise of a server and/or uploading phishing pages or other illegal content to the server, I would tend to find that staying current with security patches outweighs potential pain with plug-ins, especially in light of the fact that recent, maintained plug-ins offer one-click updates themselves.
White-hat hackers probably don’t want to risk going to prison for doing good deeds, perhaps?
Hurricane Electric is generally considered reasonably white-hat, I’m pretty sure that ne-stop.com site’s content is against their AUP, I’d suggest an e-mail to abuse@he.net with the details of it and how it’s being (ab)used, if you haven’t already sent one, and hopefully they’d nuke it.
I fired off an email to HE right after I posted this, and they nuked the site two days later.
I also sent an email to ServerBeach, host of the hacked WordPress install at devriestree.com. They responded with a “your ticket has been closed” without doing anything at all. I emailed them twice more and got the same results both times; it was not until I emailed them again with a pointer to this post that they fixed the problem and nuked the directory that was being used up to serve images for defaced Web sites.
Hurricane Electric is generally considered reasonably white-hat, I’m pretty sure that ne-stop.com site’s content is against their AUP, I’d suggest an e-mail to abuse@he.net with the details of it and how it’s being (ab)used, if you haven’t already sent one, and hopefully they’d nuke it.
One has to wonder what kind of stupid optimism it takes to think that buying stolen credit card and bank details online is a good idea.
Though I suppose if you pay for it using a stolen credit card, you’ve got nothing to lose.
Beautifully put. That contradiction always has bugged the hell out of me… Well, I guess it really did, since I haven’t believed in hell in a very long time.
One has to wonder what kind of stupid optimism it takes to think that buying stolen credit card and bank details online is a good idea.
Though I suppose if you pay for it using a stolen credit card, you’ve got nothing to lose.
I fired off an email to HE right after I posted this, and they nuked the site two days later.
I also sent an email to ServerBeach, host of the hacked WordPress install at devriestree.com. They responded with a “your ticket has been closed” without doing anything at all. I emailed them twice more and got the same results both times; it was not until I emailed them again with a pointer to this post that they fixed the problem and nuked the directory that was being used up to serve images for defaced Web sites.
Hey, have you seen this? LiveJournal, Malware, Interstitial Advertising and You.
I’m thinking of pulling up stakes and going to DreamWidth permanently; I can surf the web at work but due to the way things are set up, if the computer I’m on gets a virus, I can’t do my job. Which pretty much means I’m fired. Not a risk I can afford to take and paying for an account looks like an extortion fee right about now. And no– they won’t let us install a browser that doesn’t suck; we have to use IE goddamn 7. >:(
I hadn’t seen that, but now that I have, I’ve left a lengthy comment in reply.
This problem isn’t realted to LiveJournal at all. Any site anywhere that accepts Flash ads can potentially end up with poisoned banner ads that redirect to malware sites. The official Major League Baseball site, the New York Times site, Expedia, Delta.com, Travelocity, and other top-tier sites have all been hit with these attacks.
The only way to prevent them, short of strict law enforcement in Eastern Europe (ha!), is for ad placement services like DoubleClick to insist on receiving the source files for any Flash ad and to comb through the ad source looking for hidden redirection scripts. Microsoft does this on Bing now that they’ve been found serving up poisoned ads themselves, and other ad networks are beginning to do it too.
If Dreamwidth starts accepting ads, they will become vulnerable too.
Hey, have you seen this? LiveJournal, Malware, Interstitial Advertising and You.
I’m thinking of pulling up stakes and going to DreamWidth permanently; I can surf the web at work but due to the way things are set up, if the computer I’m on gets a virus, I can’t do my job. Which pretty much means I’m fired. Not a risk I can afford to take and paying for an account looks like an extortion fee right about now. And no– they won’t let us install a browser that doesn’t suck; we have to use IE goddamn 7. >:(
I hadn’t seen that, but now that I have, I’ve left a lengthy comment in reply.
This problem isn’t realted to LiveJournal at all. Any site anywhere that accepts Flash ads can potentially end up with poisoned banner ads that redirect to malware sites. The official Major League Baseball site, the New York Times site, Expedia, Delta.com, Travelocity, and other top-tier sites have all been hit with these attacks.
The only way to prevent them, short of strict law enforcement in Eastern Europe (ha!), is for ad placement services like DoubleClick to insist on receiving the source files for any Flash ad and to comb through the ad source looking for hidden redirection scripts. Microsoft does this on Bing now that they’ve been found serving up poisoned ads themselves, and other ad networks are beginning to do it too.
If Dreamwidth starts accepting ads, they will become vulnerable too.
Beautifully put. That contradiction always has bugged the hell out of me… Well, I guess it really did, since I haven’t believed in hell in a very long time.
If poly is more evolved, then why don’t people who stop having multiple relationships turn into weird creatures from bad Star Trek episodes? 🙂
If poly is more evolved, then why don’t people who stop having multiple relationships turn into weird creatures from bad Star Trek episodes? 🙂
TL,DR.
No srsly, I actually read it; but cut it down a bit next time. Jebus that was long.
TL,DR.
No srsly, I actually read it; but cut it down a bit next time. Jebus that was long.
This.
OKC hasn’t been a good meeting place for me – and yeah, a lot of the email i get is just crude. *sigh* I wish there was a better online site for poly folks to meet each other.
This.
OKC hasn’t been a good meeting place for me – and yeah, a lot of the email i get is just crude. *sigh* I wish there was a better online site for poly folks to meet each other.