I have a love/hate relationship with WordPress.
Actually, that’s not true. I like WordPress rather a lot, and I wish that more open-source projects had the finish, polish, and sophistication of WordPress. I own about a half-dozen Web sites that run it, and I’m overall very fond of it.
What I don’t like is the number of people who set up a WordPress install, then walk away from it and never install any updates or security patches. WordPress is a popular target for hackers, because it’s widely deployed and easy to find, and because so, so many people don’t keep on top of updates.
Which, frankly, baffles me. It’s incredibly easy to update–easier, in fact, than any open-source server software I’ve ever used. You log in to the admin area. It tells you “There is an update. Click here to install the update.” You click one button. Bang, that’s it! There literally is nothing else you have to do.
So, anyway, today I found yet another phony bank phish in my email. The phish pretends to be an HSBC Bank page, and it attempts to trick the gullible into handing out their bank account number and password. So far, so bog-standard.
*** WARNING *** WARNING *** WARNING ***
The URLs in this post are live at the time of this writing. They do not lead to malware sites, but they DO lead to phony bank phish sites.
The phish page in my email lives at
It’s a pretty bog-standard phish, a page living on a hacked server that collects personal financial information and then sends them off to the phishers via a php-to-email script.
The server that it lives on,
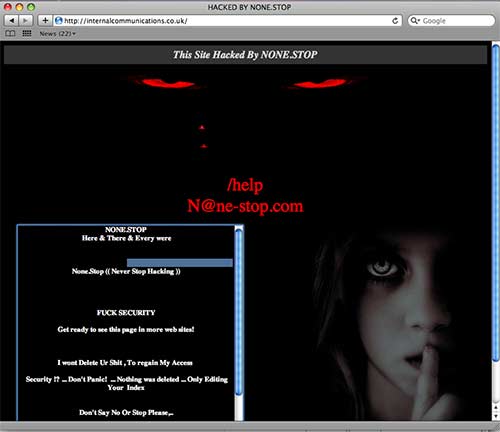
The site itself is completely defaced. The defacement left a hole big enough to drive a truck through, and the phishers put the phony bank page on the site after the person or group who defaced it hacked it and left it wide open. EDIT: The site defacer, who goes by the name “NONE-STOP,” is also a phisher who sells stolen credit card numbers, stolen bank account login information, and other stolen identity information. More at the end of this post.
The front page of the hacked site, as of the time of this writing, looks like this (click for larger):
I haven’t heard of NONE.STOP, whoever he/she/they are; as near as I can tell, there’s only one other site defacement (
Now is where it gets interesting, and where WordPress comes in.
Normally, when a site is defaced, the images that are used in the defacement are uploaded to the hacked server. Not in this case. In this case, the images used in the defacement are being remote loaded from another server.
A hacked WordPress install, that was set up a while ago, had a single test post added to it, and was abandoned.
Specifically, the images used in the defacement are being loaded from
and so on. The Web site
The site
$whois devriestree.com
Whois Server Version 2.0
Domain Name: DEVRIESTREE.COM
Registrar: GODADDY.COM, INC.
Whois Server: whois.godaddy.com
Referral URL: http://registrar.godaddy.com
Name Server: NS.NETVTECH.COM
Name Server: NS1.GEODNS.NET
Name Server: NS2.GEODNS.NET
Status: clientDeleteProhibited
Status: clientRenewProhibited
Status: clientTransferProhibited
Status: clientUpdateProhibited
Updated Date: 21-oct-2008
Creation Date: 19-oct-2005
Expiration Date: 19-oct-2010
Registrant:
NetVenture Technologies, Inc.
1490 S Military Trail
Suite 13E
West Palm Beach, Florida 33415
United States
Registered through: GoDaddy.com, Inc. (http://www.godaddy.com)
Domain Name: DEVRIESTREE.COM
Created on: 18-Oct-05
Expires on: 19-Oct-10
Last Updated on: 12-Jul-07
Administrative Contact:
DeVries, James j@netvtech.com
NetVenture Technologies, Inc.
1490 S Military Trail
Suite 13E
West Palm Beach, Florida 33415
United States
5613016666 Fax — 5618288035
Technical Contact:
DeVries, James j@netvtech.com
NetVenture Technologies, Inc.
1490 S Military Trail
Suite 13E
West Palm Beach, Florida 33415
United States
5613016666 Fax — 5618288035
Domain servers in listed order:
NS1.GEODNS.NET
NS2.GEODNS.NET
NS.NETVTECH.COM
The Web site at
Folks, seriously, update your WordPress installs. It’s automatic and effortless.
EDITED TO ADD:
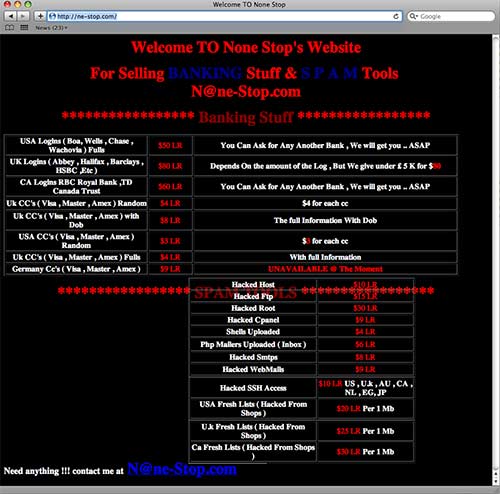
The person who defaced the Web site and who is storing his images on hacked WordPress sites has a Web site of his own, through which he sells stolen credit card numbers, phish kits, stolen bank account information, and so on. His Web site is at
hosted by Hurricane Electric.
$whois ne-stop.com
Whois Server Version 2.0
Domain Name: NE-STOP.COM
Registrar: REGISTER.COM, INC.
Whois Server: whois.register.com
Referral URL: http://www.register.com
Name Server: NS1.HE.NET
Name Server: NS2.HE.NET
Name Server: NS3.HE.NET
Status: clientTransferProhibited
Updated Date: 12-jan-2010
Creation Date: 11-jan-2010
Expiration Date: 11-jan-2011
>>> Last update of whois database: Mon, 18 Jan 2010 07:57:57 UTC <<< Registration Service Provided By: Hurricane Electric Internet Services Contact: hostmaster@he.net Visit: hurricanenames.net Domain name: ne-stop.com Registrant Contact: Ladde Weiong Ladde Weiong () Fax: 125 Club Garden Road Sheffield, S11 8BW GB Administrative Contact: Hurricane Electric Internet Services Hostmaster he.net (hostmaster@he.net) +1.5105804100 Fax: 760 Mission Court Fremont, CA 94539 US Technical Contact: Hurricane Electric Internet Services Hostmaster he.net (hostmaster@he.net) +1.5105804100 Fax: 760 Mission Court Fremont, CA 94539 US Status: Locked Name Servers: ns1.he.net ns2.he.net ns3.he.net Creation date: 11 Jan 2010 11:56:14 Expiration date: 11 Jan 2011 11:56:14 As of the time of this writing, the front page of the site looked like this (click for larger):