A little while ago, I posted about a phish scam in which someone had placed multiple fake PayPal and bank sites on one server in order to trick people into handing over their bank account information. This particular type of scam is quite common, of course; I get a couple dozen a week in my email box these days.
It’s rare to see one computer hosting multiple different fake sites, and rarer still to see them hosted for an extended period of time. Usually, the way it works is that hackers break into a poorly secured Web server (for example, in today’s crop of phish emails there’s a fake PayPal page that’s on a Web site running an outdated, insecure WordPress install, and a fake Abbey Bank page running on a hacked Web site that’s using an old, unpatched copy of the Joomla content management software.)
The fake PayPal and bank sites I discovered a couple of weeks ago were running on a server belonging to an ISP called a2b2.com, which at the time I believed wasn’t actually a corrupt ISP, but rather a single clueless individual. The ISP a2b2.com is located in Great Britain and seems to be run by just one person.
A day after I posted about that site, I received an email from the guy who runs that ISP, telling me that the server had been taken offline and the fake bank and PayPal sites were gone.
I thought that was the end of it. I was wrong.
We’re about to get technical here!
The ISP is corrupt. Its owner, Russell Foster, appears to be knowingly and deliberately profiting from phony scam Web sites.
The server that used to host the fake bank and PayPal sites is back online. It has a new Web site living on it–a Web site called No Spam Shop. No Spam Shop is a one-stop shopping site for spam tools and for software that lets you set up fake bank and PayPal sites. They also offer tools for setting up hidden, untraceable email servers for the purpose of collecting bank account information that is stolen using fake bank sites, tools for sending out phish email, and even sample email templates that look like official bank and PayPal emails.
A snapshot of their download page as of the time of this writing looks like this:
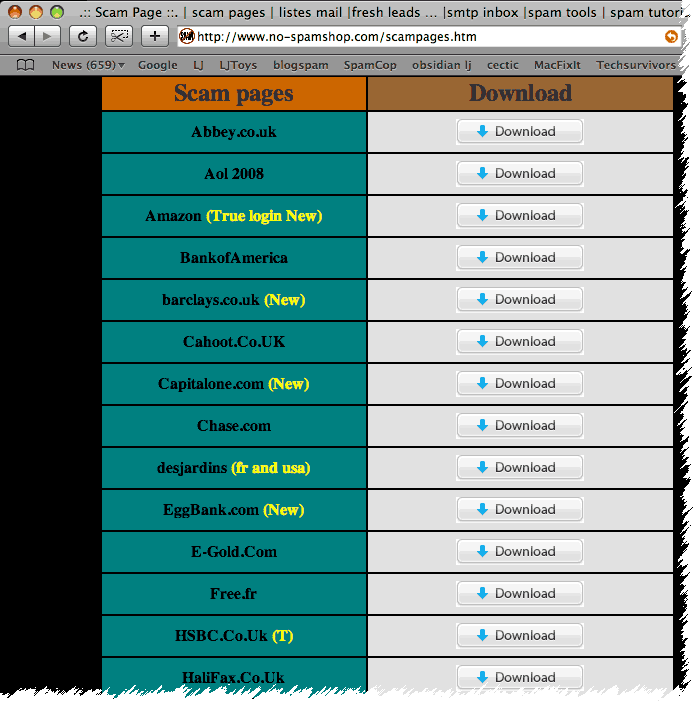
Each of these downloads contains all the files necessary to set up a phony bank site on a hacked Web server, which will ask visitors for their bank account information and then send the bank account information securely to the hacker.
The Whois for no-spamshop.com is a bit strange, in the sense that most open fraud sites tend to try to conceal their registration information. This one doesn’t, which makes me believe the registration information is most likely fake:
domain: no-spamshop.com
owner: Ruby Annette White
email: jijijoujou11@hotmail.fr
address: 11124 Doty Dr
city: Conroe
state: texas
postal-code: 77303
country: US
phone: +193.69895867
admin-c: CCOM-1358383 jijijoujou11@hotmail.fr
tech-c: CCOM-1358383 jijijoujou11@hotmail.fr
billing-c: CCOM-1358383 jijijoujou11@hotmail.fr
nserver: ns1.twixhost.info
nserver: ns2.twixhost.info
status: lock
created: 2008-11-16 12:24:38 UTC
modified: 2009-03-26 10:27:00 UTC
expires: 2011-11-16 12:24:38 UTC
source: joker.com live whois service
query-time: 0.010892
db-updated: 2009-05-21 18:26:44
The address in Texas is real. The phone number, however, is not a US number at all, so the registration name and address have no connection whatsoever to the registration phone number. Considering that the people who own no-spamshop.com are in the business of fraud and identity theft, most likely the registration information on the domain name is a stolen identity.
The domain is registered through Joker.com, a rogue registrar that makes a great deal of its money by registering domain names for spammers, thieves, fraud artists, and phishers. Joker has a long and ignoble history–it nearly lost its registrar status last year, and it’s been the subject of numerous complaints and links to spam domains. Joker.com registers only a small percentage of the domain names out there, but a disroportionate number of their domains are spam and fraud domains.
All roads associated with the domain no-spamshop.com lead back to a2b2.com and Russell Foster.
The nameservers for no-spamshop.com, ns1.twixhost.info and ns2.twixhost.info, belong to TwixtHost, an Arabic-language ISP living in a2b2 IP space at 78.110.170.227.
Yep, you read that right.
The name servers for no-spamshop.com live on the same IP address as no-spamshop.com itself (which is terrible practice, but that’s beside the point), which is living on the same IP address that has been used in numerous bank and PayPal phishes. The Whois information for twixhost.info looks like this:
Domain ID:D26226349-LRMS
Domain Name:TWIXHOST.INFO
Created On:20-Sep-2008 17:15:06 UTC
Last Updated On:19-Nov-2008 20:33:38 UTC
Expiration Date:20-Sep-2009 17:15:06 UTC
Sponsoring Registrar:Tucows Inc. (R139-LRMS)
Status:OK
Registrant ID:tuUrtnMGM22IaMYd
Registrant Name:mekh abdelmounaime
Registrant Organization:Twix Host Inc
Registrant Street1:Daksi Co
Registrant Street2:
Registrant Street3:
Registrant City:Const
Registrant State/Province:DZ
Registrant Postal Code:00000
Registrant Country:DZ
Registrant Phone:+44.021300000000
Tech Email:services@123-reg.co.uk
Name Server:NS1.TWIXHOST.INFO
Name Server:NS2.TWIXHOST.INFO
And what happens if you Google the name of the owner of TwixtHost, Mekh Abdelmounaime? Oh, look, you see that it is associated with a PayPal phish! (Technical details)
So, to recap:
Two weeks ago, I wrote about multiple phish sites being hosted on one IP address, an address belonging to a company called a2b2.com. The day after I posted, the owner of a2b2.com emailed me to tell me the server had been taken down. Now, it’s back up again, running a Web site that specializes in selling software to create phish sites, which just so happens to be registered with a phony name and just so happens to live on the same IP address as another site whose owner just so happens to be connected with other phish sites.
I no longer believe that Russell Foster and a2b2.com are clueless dupes whose inattention is being exploited by criminals. The evidence seems overwhelming at this point that Russell Foster and a2b2.com are active participants, at the very least, in a systematic, organized identity theft ring.

You are so gifted at this sort of stuff – I would have no clue where to start.
Can you leverage this information into some sort of get-out-of-jail free card should you ever land in hot water at the wrong end of an anti-sex witchhunt?
Only if history learned from Alan Turing. – ZM
You are so gifted at this sort of stuff – I would have no clue where to start.
Can you leverage this information into some sort of get-out-of-jail free card should you ever land in hot water at the wrong end of an anti-sex witchhunt?
Franklin —
You should spread this information to other groups monitoring scams, phishing, and the like. This is excellent information.
Franklin —
You should spread this information to other groups monitoring scams, phishing, and the like. This is excellent information.
Nice bit of detective work, that. What’s the next step?
Nice bit of detective work, that. What’s the next step?
awesome investigative mojo. going to report, etc.?
awesome investigative mojo. going to report, etc.?
Thank you so much for continuing to post geek erotica like this. It really brightens my day! I <3 you!!! You do great work.
Thank you so much for continuing to post geek erotica like this. It really brightens my day! I <3 you!!! You do great work.
Can you submit this information to someone in authority?
Franklin IS THE AUTHORITY!
Okay, actually I just like saying that.
Can you submit this information to someone in authority?
Franklin IS THE AUTHORITY!
Okay, actually I just like saying that.
Only if history learned from Alan Turing. – ZM
Either that, or report them to the FBI\FCC.
Either that, or report them to the FBI\FCC.