[Edit 11-Jan-2023] I’ve received a reply from Fly.io; see end of this entry
Ah, a new year has come. Out with the old, in with the new…strategies for phish and malware sites, that is.
And what would phish and malware sites be without complicit webhosts and web service providers?
So today I’m going to dive into an enormous quantity of SMS text message spam I’ve been flooded with over the past couple of months, who’s behind it, and what it’s doing.
It started in mid-November of last ear (2023), with a text message saying “The USPS package arrived at the warehouse but could not be delivered” and a link to a site that was just a random collection of letters and numbers. No biggie, I get these all the time. Standard run of the mill phish attempt. If you visit the link, you’re taken to a site that looks like the Post Office, but it’s a fake, of course. They ask you to type a bunch of personal information, which the people responsible will use to steal your identity, get loans in oyur name, whatever.
Then I got another. And another. And another. And another. And then dozens more, coming in one, two, three, four, sometimes five or more a day.
And they haven’t stopped.
Text message after text message after text message. “You’ve been infected with viruses.” “Your cloud service has been terminated.” “We couldn’t deliver your package.”
All of them with URLs that looked like random strings of letters and numbers.
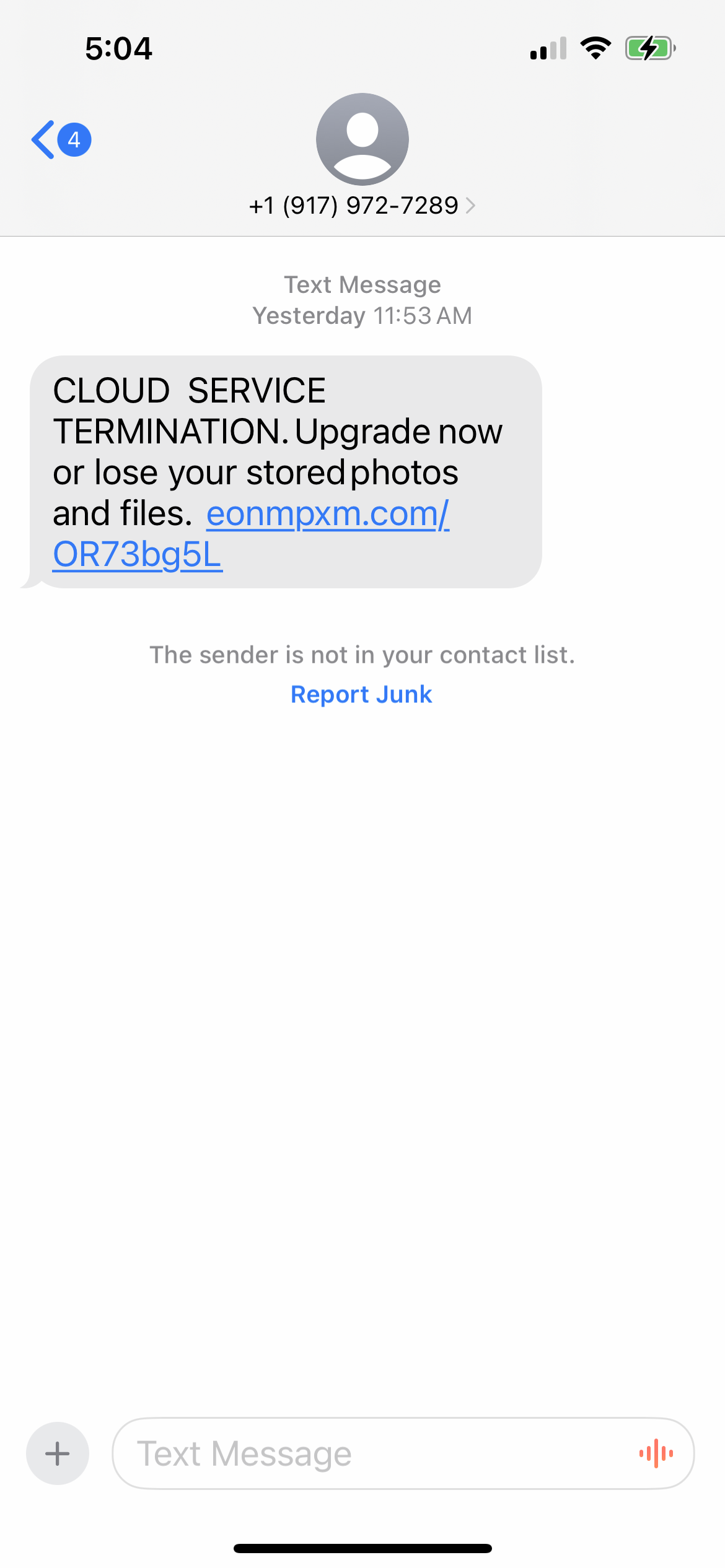
So my spidey sense was activated, and I looked up all those URLs.
Surprise, surprise, every single one is hosted on the same web service provider, an outfit called fly.io.

And there are a lot of them.
*** CAUTION *** CAUTION *** CAUTION ***
THESE LINKS ARE LIVE AS OF THE TIME OF WRITING THIS. Many of these links will bring you to malware or phish sites. DO NOT visit these links if you don’t know what you’re doing.
I started collecting the URLs from the text messages:
- http://eonmpxm.com/OR73bg5L
FakeAV malware site - http://wkcetku.com/G1LO5X38
Fake “government subsidy” site - http://nztkspy.com/MK2RVeJg
FakeAV malware site - http://lkxsxef.com/KJeQ09Vp
FakeAV malware - http://klxnitq.com/oxp18G47
Equifax phish - http://epgguli.com/0M37VmkO
McAfee phish - http://yonxutn.com/1MZbOrZv
FedEx phish - http://zveeyou.com/7Xy1E8G8
FakeAV malware - http://mirumbf.com/KJeQ09Vp
FakeAV malware - http://mirumbf.com/KJeQ09Vp
FakeAV malware - http://qjkwmww.com/yng4eExR
Fake USPS phish - http://wnddwet.com/KJe40qm5
FakeAV malware - http://pdxftwt.com/ER39R0rR
XFinity phish - http://plefaas.com/rNzdEAEW
FakeAV malware - http://oitbaon.com/A3B6vBOe
FakeAV malware - http://napiyib.com/nQ0mJKoZ
FakeAV malware - http://kozqtlp.com/vGeO0XmX
Xfinity phish - http://ugokulc.com/KJM89Mem
USPS phish - http://iqbyojt.com/KJeQ09Vp
FakeAV malware - http://sobagiw.com/nQVA0bVp
Xfinity phish - http://oosjrjt.com/GRG8ML9n
FakeAV malware - http://xqzfnuh.com/ZjgL4GbE
Xfinity phish - http://tecvxzo.com/5aannZO7
Google phish
I notified fly.io’s abuse team about the problem. And notified them. And notified them. And notified them. Each time, I received an identical reply, from a guy calling himself “Matt Braun,” saying only “I have let our customer know. Thanks!”

Matt Braun doesn’t appear to have grasped that their customer is the phisher. And lately, I haven’t even received these replies; they haven’t acknowledged recent abuse reports in days. Meanwhile (of course) all the links remain active because (of course)…their customer is the phisher.
Okay, so how does the scheme work?
I’ve spent some time mapping out the network. The quick overview:
- A text message is mass broadcast, advertising a URL on fly.io.
- Marks who click on the link in the message are redirected to a site called “track.palersaid.com,” hosted on Amazon AWS. Track.palersaid.com looks at the incoming fly.io URL, the type of computer or smartphone you’re using, and probably other stuff, then sends you on to another site.
- This site, track.hangzdark.com, is another tracking and redirection site also hosted on Amazon AWS.
- From there, marks are redirected to the actual target site, which might be a fake FedEx page, a fake UPS page, a fake “virus scan” page, or more. There are a lot of these destinations: read.messagealert.com, kolakonages.com, aca.trustedplanfinder.com, and more. Some of these destination sites are, no surprise here, hosted on Namecheap, which is in my opinion one of the scuzziest of malware and spam sewer hosts.

Example destination page
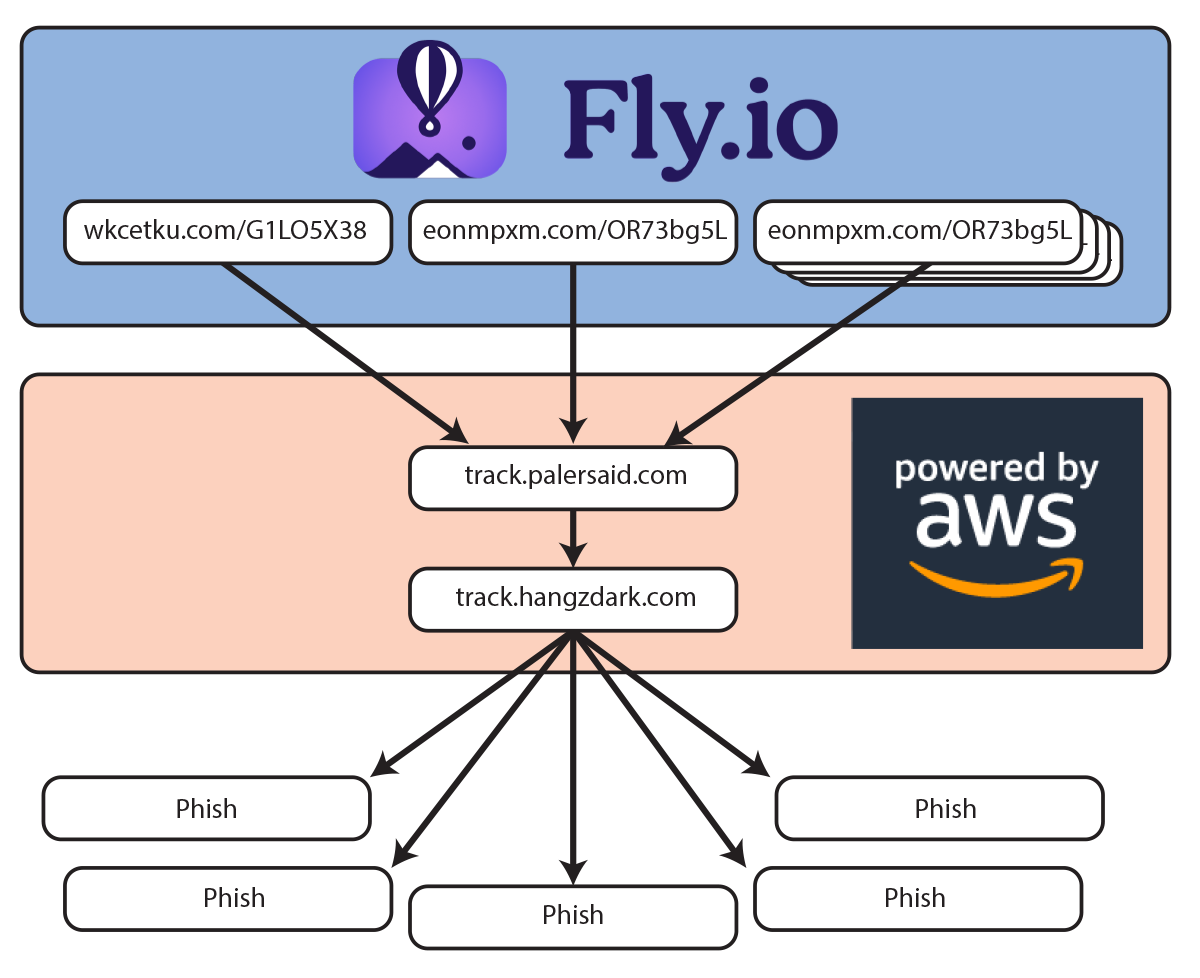
How the network works
This bears a strong resemblance to some of the malware and spam networks I’ve mapped out in the past, though the delivery network (SMS text messages) and the web service provider (fly.io) are different.
If you get these text messages, do not follow the links. If you are also seeing these messages, please let me know in a comment! I would love to know how big this network is. Fly.io seems reluctant to shut down these phishers, which leads me to wonder if they aren’t making quite a bit of money from them.
[Edit 11-Jan-2023] I’ve received a reply from Fly.io’s Abuse team:
Thank you for your patience with us over the holiday, and some follow up details.
Usually, when we have reports of spammer or abuser on our platform, our internal systems have a host of signals that we can look to to verify the report and take the appropriate action. In the vast majority of cases the signals are clear and unequivocal. However, in this instance, the signals were entirely the opposite: all signs pointed to a seemingly-legitimate user.
Our systems are set up for “either you are a customer or you are not”, and banning a customer would mean immediate and irrevocable loss of that’s customers data. That’s is not a risk we take lightly so we were not going to flip the switch and risk blowing away someone’s information without a smoking gun. I expect you and I have both seen dozens of those posts on Hacker News or elsewhere where an innocent user writes “Company has deleted my entire account without warning and I’ve lost years of data”. We don’t want to do that to someone.
So where does that leave us? The apparent reason for the behavior/signal disconnect is that it was our customer’s customer doing the abuse. Our customer has committed to evicting their customer today which should put an end to the redirection through our systems (though, unfortunately, I don’t expect that’ll have any impact on the SMS spam). If it doesn’t resolve things, let us know. We’re back online after the holiday and more in a position to chase things things down.
Additionally, there were two other concerns we need to address internally:
1) We don’t have the ability to suspend users. This is something that I’m going to pursue as we need something more nuanced than our all-or-nothing approach so that we’re able to move on complaints sooner without risk of harming someone innocently caught in the middle of things.
2) We did not follow up with the customer as often as we should have after their initial acknowledgement of the problem and indication that they would address it. That’s a coordination process breakdown exacerbated by people taking time off during the holidays and not having the usual “obviously-abuse” signals. Additionally, we need to come up with an approach to our abuse ticketing system that allows for long-lived cases.You can email me, personally, if you feel you aren’t getting attention on this (email redacted) and I’m sincerely sorry for the delay in letting you know where things stood or getting things sorted with the customer.
It seems Fly.io is one of the good guys.
The spam stopped for a few days, though it has resumed again. This time, the SMS spam domains are hosted on Alibaba rather than Fly.io.

I’ve been getting texts that seem similar. I’ve been “report[ing] junk” through ios and deleting them. I don’t want to touch them, because I don’t know what I’m doing. Thanks for all your hard work. I hope it helps in this case.
Yes! I get the post office one about 4 times a week. I’m in California.
Shari