Right now, I am in the remote cabin in the woods where we wrote More Than Two, working on two new books: a nonfiction book called Love More, Be Awesome and a novel called Black Iron.
The cabin has very limited Internet access that’s approximately the same speed as old-fashioned dialup, so fetching email is always a bit dicey. Imagine my disappointment at the timing, then, of a large-scale malware attack.
The emails are all very simple: just two lines and a bit.ly URL shortener address. They come from a wide range of IP addresses with a large number of different forged From: addresses, and they all look exactly the same:
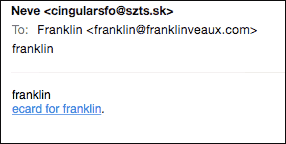
The system behind this email, however, is anything but simple.
The Network
The emails all contain a URL shortening address that uses the popular bit.ly URL shortener service. There’s a complex network behind that short URL, that does a number of different things: promotes dodgy products such as supposed “brain boosting” pills, and attempts to download malware and trick people into phoning phony tech support Web sites that scam victims for hundreds of dollars in fake tech support charges (and also dupe victims into downloading more malware).
All the sites mentioned in this post are live at the time of writing this. Most of them will attempt to download malware or redirect you to sites that attempt to download malware. Do not visit these sites if you don’t know what you’re doing.
When you click the link in one of these emails, you’re redirected via several steps to a site called wholesoil.com that then sends you off to one of many, many possible destinations, some of which are typical run-of-the-mill spam sites and some of which are malware sites. The network looks like this:
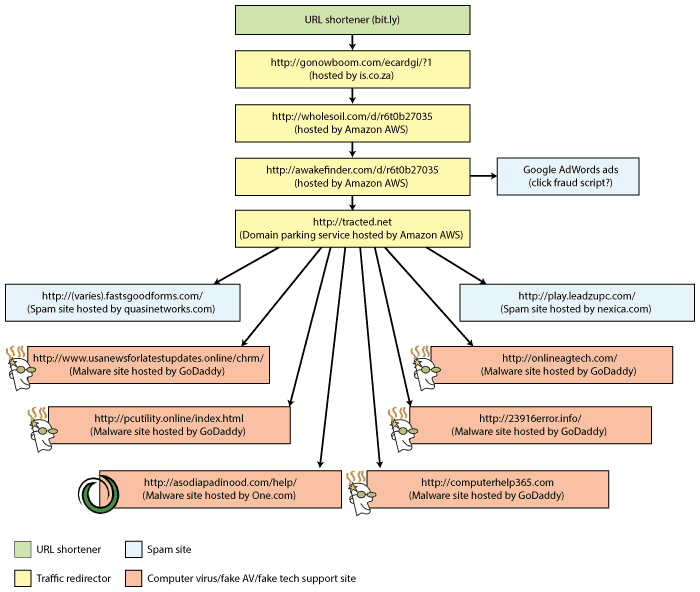
This chart is not complete; there are many, many other malware sites that you may be redirected to. I charted well over a dozen more such sites before I quit looking.
Clicking on the link contained in the email enters you into a lottery of suck: Will you get spam? Will you get pwn3d? Hard to say!
I’m not 100% certain it’s entirely random. There may be some element of looking at the browser’s user agent or the visitor’s IP address; visiting wholesoil.com repeatedly in a short span of time will tend to result in getting redirected to the same spam URL over and over after a while.
The people behind this network have gone to considerable lengths to hide themselves. For example, one step of the redirection happens via a domain parking service called tracted.net. The redirection script that relays traffic through this site scrubs the referrer header. When you travel from one Web site to another, your browser sends a “referrer header” that tells the new site where you came from; this is how people can tell where they’re getting traffic from. But this network carefully removes that information, so that the owners of tracted.net can not easily detect this traffic.
The most common spam destination is a subdomain on a site called fastgoodforms.com. These subdomains change often: 570-inteligen.fastgoodforms.com, 324-brain.fastgoodforms.com, 923-inteligen.fastgoodforms.com, and so on.
But more often than spam, users will get redirected to a phony tech support page that displays a fake Windows error message. These sites look like this:
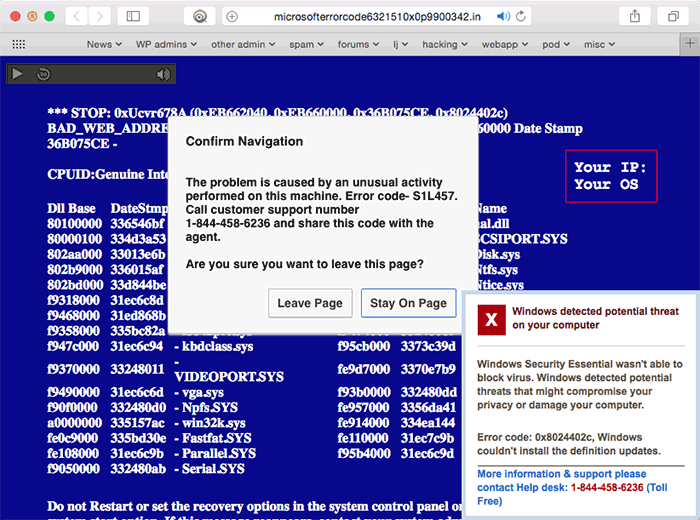
These sites attempt to download malware—specifically, a remote control program that allows attackers to take control of an infected computer. They also attempt to prevent the user’sWeb browser from leaving the site, and display popups over and over and over again telling the user that the computer has been infected by a virus and to call Microsoft Support at a toll-free number.
The toll-free number is owned and operated by the scammers. If you call it, you’re sent to a person in India who will attempt to get your credit card number, and will try to talk you into installing software on your computer to “fix” the “problem.” This software is, of course, remote control malware.
How the mighty fall
While I was tracing out this network, I discovered many, many, many of these fake tech support Web sites that are being used to spread malware and try to con users.
And that’s where I noticed an interesting pattern.
The overwhelming majority of these malware sites are hosted, not on dodgy services in China or the Netherlands as you might normally expect, but on GoDaddy.

Not all of the malware sites are hosted on GoDaddy (I found one hosted on One, one hosted on Hostwinds, and one on IX Web Hosting, for example), but the vast majority—literally dozens—are.
I believe that GoDaddy is the choice of malware hosts because their abuse and security teams, which once upon a time had an excellent reputation in the Web hosting industry, have been pared back to the point they can no longer keep up…or perhaps simply no longer care. (GoDaddy was bought out by an investment group a few years back, which is when its reputation began to decline.)
I reported the Hostwinds-hosted malware site to Hostwinds abuse; it was removed about ten hours later. I reported the malware site on IX Web Hosting; it was gone in 17 minutes. But malware and phish sites on GoDaddy remain, in my experience, for an average of about a month before GoDaddy acts, and spam sites remain essentially forever.
Spammers and malware distributors are adaptable. They move Web hosts often, leaving hosting companies that take rapid action against them and congregating on tolerant sites that permit spam and malware. I suspect the fact that so many malware and fake tech support sites are hosted on GoDaddy is a consequence of the indifference or inability of their abuse and security teams.
To be fair, if you make enough noise, GoDaddy will eventually act. I have engaged with GoDaddy on Twitter, and when I do that, they will generally take down a site I complain about within a few days. The dozens of other sites, however, remain.
I am currently a GoDaddy customer. I do not use GoDaddy for Web hosting, but I do have a large number of domains registered there. I intend to begin removing my domains from GoDaddy, because I do not like supporting spam-tolerant companies. (Ironically, this was the reason I left Namecheap to go to GoDaddy; Namecheap is owned by a company called Rightside, that has become notorious for willingly hosting some of the biggest players in the spam business.)
So if you have a domain registrar you use, please leave a comment! I would love to find a replacement for GoDaddy and pull all my domains away from them. (If you’re using GoDaddy for Web hosting or domains, I advise you to do likewise, unless you fancy staying with a company whose approach to security and malware is so lax.)
I would also like to invite GoDaddy representatives to offer their side of the story in the comments as well.
