About three months ago, I got an email telling me that my FedEx package couldn’t be delivered. The body of the email told me that the UPS courier tried to deliver it, and that it would be sent back if I didn’t click on the attached link.
Naturally, as I wasn’t expecting a FedEx pacakge, and given that FedEx presumably knows it isn’t UPS, I knew immediately that clicking the link was a Very Bad Idea…at least on an unsecured Windows box. Sure enough, clicking it downloaded a Windows executable, which VirusTotal identified as W32/Kuluoz, a backdoor command-and-control software that also attempts to download other malware.
I reported the site hosting the malware and forgot about it.
Then, things started to change.
I’ve been getting more and more copies of this email lately; I’m now averaging several a week. The silly error and grammar mistakes have been fixed, and the emails now look quite polished. Here’s an example I received a couple of days ago:
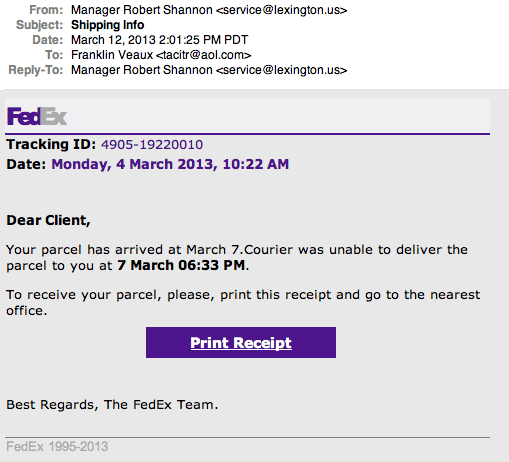
The “Print Receipt” link leads to
CAUTION *** CAUTION *** CAUTION
The links in this blog post ARE LIVE as of the time of writing this. If you attempt to visit them with a vulnerable Windows computer, they WILL try to download malware to your computer. DO NOT visit these links if you don’t know what you’re doing!
The site 123goplus.com belongs to a company that produces business cards and similar printed pieces in Montreal, Canada.
$ whois
123goplus.com Whois Server Version 2.0
Domain Name:
123GOPLUS.COM
Registrar:GODADDY.COM , LLC
Whois Server:whois.godaddy.com
Referral URL:http://registrar.godaddy.com
Name Server: NS1.MTLEXPRESS.CA
Name Server: NS2.MTLEXPRESS.CA
Status: clientDeleteProhibited
Status: clientRenewProhibited
Status: clientTransferProhibited
Status: clientUpdateProhibited
Updated Date: 06-jan-2013
Creation Date: 06-may-2006
Expiration Date: 06-may-2014>>> Last update of whois database: Thu, 14 Mar 2013 22:32:30 UTC <<< Registrant: Pierino Pezzi 8630 Perra #3 Montreal, Quebec H1E5M8 Canada Administrative Contact: Pezzi, Pierino
creationexpress@yahoo.com
8630 Perra #3
Montreal, Quebec H1E5M8
Canada
+1.5142741616Technical Contact:
Pezzi, Pierinocreationexpress@yahoo.com
8630 Perra #3
Montreal, Quebec H1E5M8
Canada
+1.5142741616Domain servers in listed order:
NS1.MTLEXPRESS.CA
NS2.MTLEXPRESS.CA
The site
Here’s where things get cool.
Visiting this URL from a Mac browser or a Linux browser returns a 404 Not Found page, presumably to fool folks like me into thinking that the problem has been fixed.
Visiting the URL
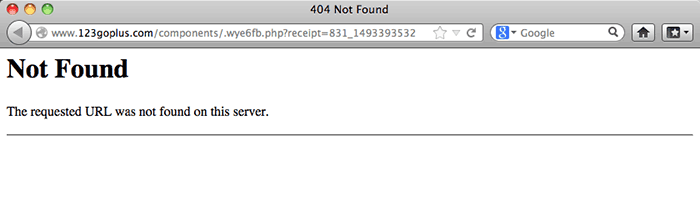
But hang on! Let’s go to
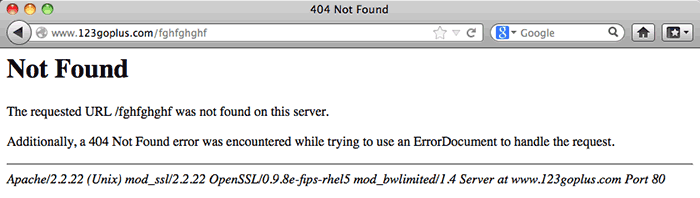
See the difference? The 404 error that you get when you go to the malware dropper is phony. The malware dropper is there, and it does live at that address.
If you visit the malware dropper with your browser user-agent set to, say, Internet Explorer 6 (God help you), you won’t see an error message. Instead, it will download a .zip file called “PostalReceipt.zip”.
I have downloaded several copies of this file from several different compromised hosts over the past couple of months, all of them from nearly identical FedEx emails.
The payload sites vary. Many different sites have been hacked and used to download this malware:
In every case, the site is running an outdated, insecure copy of WordPress or Joomla. The hackers hack the site (which is trivial to do), place a PHP script that downloads the malware, then send out a bunch of these phony emails about a non-existent FedEx package, hoping to trick people into clicking the link.
Most of these sites remain infected, weeks or months after being reported to the ISPs, because either the ISPs don’t care or the ISPs aren’t paying attention to the fact that the malware scripts return phony 404 pages. (GoDaddy and OVH, I’m especially looking at you here.)
The people behind this attack are adapting the malware rapidly. I downloaded three samples of the PostalReceipt.zip file, one on January 25 aqnd two on January 30, and they differ from one another. VirusTotal identifies the earliest one as W32/Kuluoz, the second as W32/Kuluoz.B, and the third as W32/Kuluoz.3.
There are some interesting things about this attack.
The group–and I bet it is a group–of criminals responsible for this attack are taking care to cover their tracks and to keep abuse teams from removing the malware from infected sites. Each spam email contains a code at the end of the malicious URL, and the URL returns a phony error message if it doesn’t see a valid code.
The virus downloader script is smart enough to examine the browser user-agent to see what kind of computer and what Web browser the victim is using. If it sees a browser or a computer that it can’t exploit, it returns a fake error message.
Only if it sees a vulnerable browser does it attempt to download the malwarewhich then surrenders the computer to the control of the hackers.
The malware droppers are installed, probably automatically, on sites running insecure WordPress or Joomla software. The phony 404 error messages slow down the Web hosting companies’ response, so the malware droppers stay active for long periods of time.
I’ve said it before, and I’ll say it again: If you run a Web site that uses a content managemet or blogging or ecommerce package, you *** ABSOLUTELY *** MUST *** check periodically for software updaes and install them immediately. (When a software update comes out, the organized crime gangs that do this kind of attack will analyze it and figure out what security holes it patches. Within days, they will start taking over any Web site that hasn’t installed the update.)
The fact that malicious scripts will cloak themselves behind fake error messages means that you can never trust that a problem has been fixed just because you see a 404 error if you try to look at a suspicious URL.

Useful information! Thanks!
Useful information! Thanks!
(When a software update comes out, the organized crime gangs that do this kind of attack will analyze it and figure out what security holes it patches. Within days, they will start taking over any Web site that hasn’t installed the update.)
Wait, are you saying that the hackers use the updates themselves to identify the previous security holes?!?
Ingenious. I never thought of that. Damn my vanilla brain.
(When a software update comes out, the organized crime gangs that do this kind of attack will analyze it and figure out what security holes it patches. Within days, they will start taking over any Web site that hasn’t installed the update.)
Wait, are you saying that the hackers use the updates themselves to identify the previous security holes?!?
Ingenious. I never thought of that. Damn my vanilla brain.
Huh that’s too bad. GoDaddy used to have a great reputation for dealing with problems.
K.
Huh that’s too bad. GoDaddy used to have a great reputation for dealing with problems.
K.
Congratulations to both of you!! 🙂
And lovely photo!
Congratulations to both of you!! 🙂
And lovely photo!
I love it, but you forgot one thing…”Faire Flings” are not on there, and they should be. 😉
I love it, but you forgot one thing…”Faire Flings” are not on there, and they should be. 😉
Tried this 4 or 5 times and never felt anything more than a mild tingle. Was somewhat disappointed…
Tried this 4 or 5 times and never felt anything more than a mild tingle. Was somewhat disappointed…
I’m not quoting everything in the 90 minute documentary. They talk about the obvious impact basic needs being met.
Hate the stats, complain about the research..watch and critique the documentary if you want, that was not my point. I still don’t think privilege equals “good life”.
I’m not quoting everything in the 90 minute documentary. They talk about the obvious impact basic needs being met.
Hate the stats, complain about the research..watch and critique the documentary if you want, that was not my point. I still don’t think privilege equals “good life”.