Note: This post is a followup to the one here describing a coordinated attack on sites running WordPress.
My friend’s WordPress sites are still partly out of commission, following the sophisticated attack by pharma spammers that I talked about a few days back. Google has listed them again, though Google’s cache still shows some of the pharma spam. I’ve been continuing to investigate the attacks, and I’ve learned some new and interesting things about these attacks…including the fact that they are moving beyond WordPress and beginning to target another popular open-source platform, Joomla.
The first thing I did was start compiling a list of sites which have been compromised by this particular hack attack. To do this, I used Google’s site: command to get a listing of what my friend’s site looked like from Google’s point of view. The site: command can be used to get a list of how Google has indexed a site; for example, if you type
site:xeromag.com
into Google, you’ll see how it has indexed all the pages of my site. Next, I took unusual words and phrases from the pharma results in Google, and searched for those exact phrases. This gave me a list of tens of thousands of sites.
I then went down that list looking at each site. If I didn’t see any trace of the pharma spam keywords in the site, I did a second Google search, this time using that site and those same pharma spam keywords. I clicked on the Google link for those results and watched what happened. If I got redirected to a pharmacy page via a redirector at googl-analize.in, I knew it was the same attack, and I added that site to my list.
For example, here is what happens if you type
site:gregatkinson.com
(one of the hacked sites I found) into a Google search.
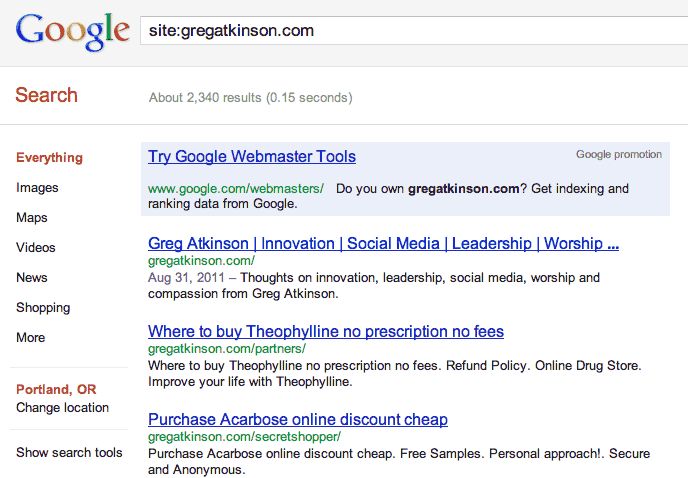
If you click on any of those links, you will not see any pharma spam. However, if you do the search AGAIN, this time using
theophylline site:gregatkinson.com
as your search term and you click on any of the links, you’ll be redirected to a pharmacy spam page.
Once I had built a list of affected sites, I then looked to see who their Web host was, and what content management software they were running. Nearly all of the sites were running WordPress, most of them fully updated and patched.
Nearly all. Not quite all, however. Some of the sites I found, I discovered, were running Joomla. This surprised me, and I think it helps rule out a zero-day exploit in WordPress as the attack vector. unless we are to believe that this one group of hackers has found and is exploiting identical zero-day flaws in both WordPress and Joomla and are attacking them the same way, which is possible but unlikely, I think the logical conclusion is that the attack vector is somewhere else.
Here’s the list of hacked sites that have all been attacked by he same person or persons who attacked my friend’s site that I’ve compiled so far:
Unless otherwise noted, the sites are running current WordPress installs.
As of yesterday, each of these sites would redirect via
*** WARNING *** WARNING *** WARNING ***
The sites googl-analize.in and sliceblogz.com are live as of the time of this writing. It appears that visits to this site result in blank pages unless the http-headers are set exactly right. However, these are sites that are being used in current hack atacks against many Web sites. I do not recommend visiting them.
I also discovered something else interesting. When I did Google searches for the exact phrases used in the WordPressand Joomla pharma spam hack attacks, many of the results I got were blog comment spam on various blogs. The blog comment spam is pretty straightforward; it was just your average, run-of-the-mill “buy cheap drugs here” rubbish with a link to a Web site.
The blog comment spam linked to
Those suspicions were confirmed when I did a Whois lookup on both sites.
| whois googl-analize.in
Domain ID:D5239480-AFIN Registrant ID:TS_16281729 Name Server:NS1.REGWAY.COM |
whois dwnloadz.in
Domain ID:D5093036-AFIN Registrant ID:TS_16281729 Name Server:NS1.REGWAY.COM |
It seems pretty clear to me that the same person is responsible both for blog comment spam and also for these attacks on WordPress and Joomla. It also seems to me that this person is quite busy tending his network of hacked sites; the behavior of the sites (now redirecting via sliceblogz rather than googl-analize.in, for instance, shows that he is able to make changes to the sites he hacks after the attack code has been installed).
The sliceblogz site is protected by private whois registration. It seems unlikely, though, that “Anatoly Vasserman” is the attacker’s real name.
Yet another surprise came when I examined the code that the hacked sites fetch from googl-analize.in (and presumably now from
Fortunately, a friend of mine recently showed me how to use wget to create arbitrary headers. When Google indexes a hacked site, the modified code serves a special page to Google’s spider; here’s what it serves up.
