A few days ago, I leveled a Horde frost mage to max level in World of Warcraft. Anyone familiar with the game knows exactly what happens next: the mad scramble to gear up a new Level 60 to be able to run mythics and raids, so that you can get even more loot to run higher-level mythics and raids…thus does the MMO hamster wheel go ’round and ’round.
So I did what every newly-minted level 60 does, of course: I turned to Google. My new 60 has a rather abysmal heirloom staff, so my first priority was finding the best way to loot better weapons.That’s when it started.Take a look, dear readers, at this Google search, and see if you can tell me what’s peculiar.
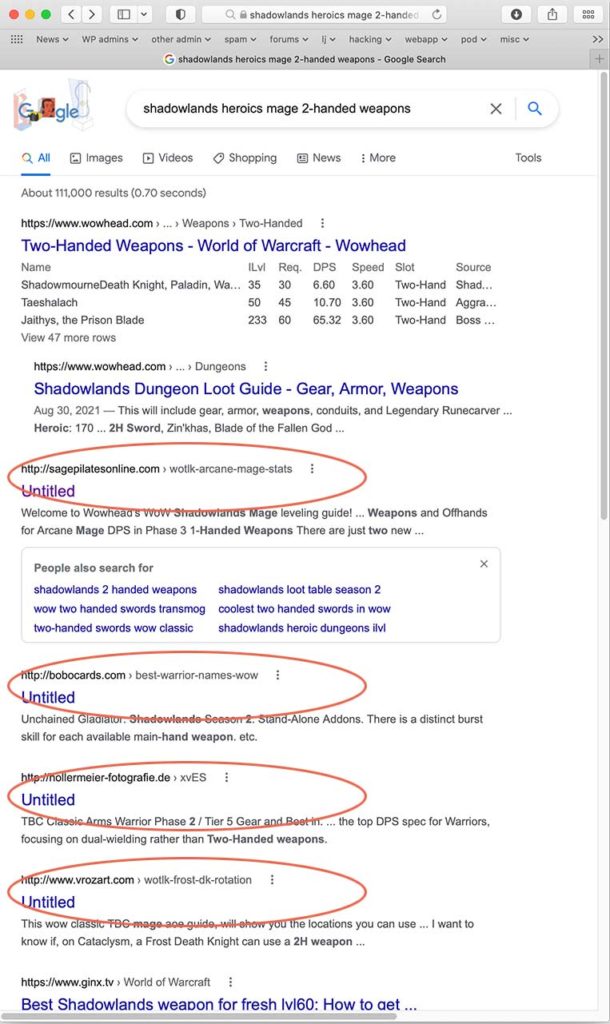
These results outstrip some of the most popular WoW sites on the Net, which is a bit peculiar itself…but more to the point, what are they doing on a site about pilates? And a German photography site? And why are they all called “untitled”?
Curious, and smelling something weird and sinister, I did what I always do when I see something that might be the tip of some kind of mass hack or compromise: I clicked on the links.
And each one of them bounced me back to a new Google page.Even more curious, I copy-pasted one of the links (after unmangling it, of course; damn you, Google, for mangling link URLs in your search links), and saw:

This is a “keyword stuff”—a page designed to appeal to Google, not to any human reader, simply by being crammed full of popular Google keywords and search phrases.
But look at the bottom of the page. It’s a bunch of randomly-generated three-character links.Curiouser and curiouser.Now well and truly engaged, cup of tea forgotten next to my keyboard, I logged out of WoW and fell down the rabbit hole.
Where do those links point? To other pages stuffed with keywords, of course.

This is how these results ranked so high in Google Search, above even well-regarded WoW sites like Icy Veins: Automated black hat SEO. Each page is populated with automatically-generated links to other pages also stuffed with keywords, which in turn point to still other pages stuffed with keywords…at least hundreds, possibly thousands, in all.
But why?The ‘why’ is suggested by some very peculiar behavior of these pages.
So. Clicking on one of these links from Google bounces the user (me) back to Google. I was browsing from a Mac, so that’s quite common—malware droppers frequently are PC specific, and will check the browser user-agent to see if it’s a Windows browser before going off to the payload site.
So I set my browser user-agent to Firefox for Windows and clicked the Google link again.
Still got bounced to Google.Hmm, interesting.What about the links at the bottom of the keyword-stuff pages?
I clicked on a few of them and was taken to other similar pages stuffed with Google keywords, so I started compiling a list, to get a sense of how big the network is, and to send to the Web hosts of the affected sites.Then something even more peculiar happened.One of the links bounced me through a whole chain of intermediaries to this:

This is, of course, a bog-standard malware dropper, that downloads malware disguised as an Adobe Flash player update.Two things to notice here:
- This page is using Mac graphics and offering a Mac DMG file (I had reset my browser user-agent to a Mac browser at this point); and
- It didn’t happen with every link click.
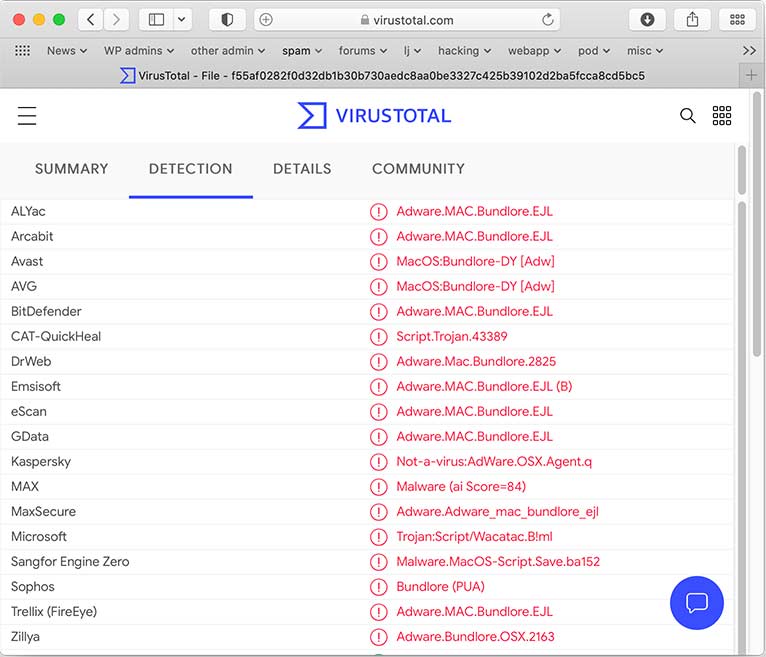
I accepted the offered download. It downloaded a Mac disk image called “AdobeFlashPlayerInstaller.dmg” (SHA hash be3b0172cd206a5196714def29dfdea1db6c6b97df009c484769db8e348d0f29) which VirusTotal identified as OSX.Bundlore:
The payload itself downloads from an Amazon S3 bucket. This one downloaded from a (now disabled) S3 bucket at
https://s3 (dot) amazonaws (dot) com/83171197-a8ce-4f88-b55a-cb1b1d3e64/k6h/33E4A3B6BB3677B313A2CF90257F93FC/c5rWf/sgWQ1F/23y2J/JRxq7yri
Okay, so.
The people behind the malware place pages loaded with Google search terms and keywords on various sites. The sites link to other sites, which link to other sites, which link to other sites. Most of the time, if you follow those links, you end up at more pages full of keywords. Sometimes, if you follow those links, you end up at malware droppers, at least on a Mac browser.But that raises a ton more questions:
- What happens if you visit from Windows browsers? Do you still get shuttled off to Mac malware droppers?
- What are the sites hosting these keyword pages?
I opened one of the keyword pages in a browser window with a Mac user agent and the same page in a window set to a Mozilla on Windows user agent and started clicking links.
One time out of every ten or so, apparently at random, the link will redirect to a page hosted at dec-info (dot) ro, then from there to
take-bestprize (dot) life/?u=fn7nu1c&o=m0gpe9l
and from there to
https://vlhriy (dot) standwearsign (dot) top/web/?sid=t4~2ydmbkjzfoczl4xn2yvekuoyhttps://dphteg (dot) postmybear (dot) top/ndpmnfiy/?u=fn7nu1c&o=m0gpe9l&f=1&sid=t1~3hnrura4uburofik5cbgqehe&fp=HuQJwbcWGjDln5Ew2hToyW0CBw1kjyv3FeSkpX03e0upmhinbK8XHPEYqwRaYVeXtj3MM1t6XrZeqRJO2rJlsa%2FU4rvLhqzkPF68ClGV%2BgG8aAAeVi1%2BVzpfqKc1%2FgzqJkYUim%2FA5%2BeZJTSlsliPcqgF%2BUGtSf4HVtqccw5htR3Qdr1HOrBgVot0x3OqXm8BCZXmtPabpYCPBkDrI6fON4t2BD%2BLq%2F8StxFAhJ%2F9IRJXm%2FgDeeUEZ3M8QP2GADwJpUOL%2BrSFGOj1ek7TLG%2BqSFD0g0NYLNAD8MSLzgvs93ZxdNRO0ffQTb4tr77puXaBjxLFqWStH5wG3MjfmlP1aU9IS9OIXQVobvyOXVd9bnDWKolMMx1QiXEjVjfJkugZAxwpeCRAUaMQTEVaTlY2OvEUT1O3gl5oe6qp7aa6nelB0TBUU60LPFmea5qMtMCm44kF%2FhAG9iEPvVxGn%2FK1yHpP0BUgpQ3frW7tIi7QTg%2Bs5A3Vdzfe%2FB3AtNhZKQSyMBTvilRWoFgVj%2FaiJeMO0QwwicxaFw7m0JvMQ2xHNmFi6bLVt9Y0YDmuk18k4vLijKBIMm1jvAAI1%2BD9MnwIxX%2FldfLjhVoJI9gOjo0V2g9Fej5Cd13Y8yzKOXeLiGB2q9et5fvKY8jy%2BgYIIfeuZJnRoMrdf2jyN592oU%2FzyXb%2BvvMp0jMgwjy0FC4YVypH9rC5L0GVqySA6HxSVS3IY4ipQJ4ejpjlWXPALS1AJJFGMYa4cSQVxqH%2Ft2UD6vcb1zwKcUKFpOxXwXCXvyTcw%2BuZt5Ihjhh1EHuSwm11rmzyrhHbGcX1DmcKOEtB1CDGXalVUxCd1007nQasfsEs4PsowLzXW2kEYlXSK%2BMXBm5hTky9dBtDEE0Z2kXqm%2F23gj1vTjdaTdokT8TLcJvFp6YUiS%2BYCwPt2wG86tn%2B8JTW7xX4ZV%2BkLNMp5lGyUGJMykDNBh7Apnumf25grNVOogynutNm6hokN5%2BV03JKtWyk%2BruOvJyjsZIy3pG6gs17nINSb2WK3tceNjm%2FXlJGQipyUUyO5AyhnEVS2TgTB502wn8%2F0tgerEizJG5055rFlsnUC994h2l87SwwAkPk%2Bp6QdxuYntNJ1DlGdRNEGjfr13GCZaUGIPO7xK6iK9HiRxJbUFoWLFR5qkGpPd1CQWTcz2VUArEG7LD97Dv%2B2NUUTFFypcxr0L05ry9t40wl0W3JSspI023cBX6E86gkw2u6b29twseC5uZkLuO8FF%2BkFjuoeMLsYLTmtvRZFHRwYH7mr2Nhh%2FcDr%2F1uG8YBTqPG8MJRGU0TFGDKpVwDBzkjOZ5zFW1VS6GU7weMF5lAlI3v4DIWHU06VgC7VMq8CanAEUUAYipXjbgHQ9zHAC5IUYhMhh3O07fv64z7R4cTF7rLb9FKojAnB1mw3OFGqTyfiQg4U4w7FyH5fpInVN7KLKgYZY2mVb%2ByZWqZztzzyyJ5ShCL44x7NXRJ19db5HnsYm5GF%2BIUX0A4lzmLNC%2F4gH60TyahFy5SF3D5SV5bBxnyyZ1atj6kwSoWHdHORx30Xv%2BBOztVKKx0rjIUdGNKEoE%2F6WMkRp3Rn9MZMNebLozLAnrKDTGxMK9Wu2fgFXvx63dDsepEbkafv1khW%2Fi92MjymBHwHDqwCn0AMpilZtYxMwF0rTjXEMmRW%2BHiPeMqorwPentz%2Bhw%2BD906VtJbzLCHrLpjHihAUtjahbOZO%2BaHIHfYwrYhWUbG36%2BMlz%2Fv27h5lBjC0ecvLXsM3fM%3D
and from there to
jjmdzb (dot) thirdfinalspeech (dot) top/ijranrwo/?u=fn7nu1c&o=m0gpe9l&f=1&sid=t1~3hnrura4uburofik5cbgqehe&fp=HuQJwbcWGjDln5Ew2hToyW0CBw1kjyv3FeSkpX03e0upmhinbK8XHPEYqwRaYVeXtj3MM1t6XrZeqRJO2rJlsa%2FU4rvLhqzkPF68ClGV%2BgG8aAAeVi1%2BVzpfqKc1%2FgzqpM0KoNuZfS3G4U2VUT4zLJuY2HK3YLKbMPQApB0aOPSFMEqxMu7p9Z9iLdxrGgD4VaxgBoAU0NVUwCzhS419JaZIx1Nn%2Fh5qvZJ0cp91ZKwNJ9oaf3JBs1ang8nVvztvojDTY9QgSofGv8yGDhzCMH5dOIqQWRp8zoGsMQhdG2%2BA8MIe%2BHC8Z1EJ1nL2D%2Fdy1Z0vT7ZPByF2yVcjMled7dac5w%2BGX1KWiRRDVJZJHDCvXRnZ4HFF1WnbPeKc06ICWJBJ7nujXBpCJ9uUpPXOunObX%2Bv%2F8L95vVW0Ha6j9hvefCeHUPqgjF75fnzUjMQmrSojwhC8gTOszDm7zKb50h33vz9qIuIVvBYZLbd8jwTyDQJBNgNytzbuOm7PxXzH8I5oeQPByR6qbvXqvqAoTZ0u3Cxk8lm5fICr0KHKpfrwj9MdiYXqRA8FeN%2Bik%2BdM%2B2Cc8aYrD8GqcI21iXh62ixJ%2FHIvp0J1bvc%2F1fR0IJ7L9v1SJq2GLLVi3S4YQMluJicCZgf0VGVO7772Np34EY5XRFeDQTDqW4niO3xy3El3uBY%2FsD%2FnJGQNEY6iH22iwOQa1twV1dvqXWi%2BmPDP0tetxDUWWH%2BaP7pv50ULa%2FmUkQF5oCVw6T0dim1JSY6WqoMx8nouj8tvwXZPS1lWPpN1mkXQdUf9I%2BYHaM2GLxWA6WvXBvJASHBF13mJXI5UsDi74StPWuqY1z0XtgqCllUVe7ar0XVyUBfYR%2FZqEGwdBKMyaCtYnB2uCLlqP9P8btyTAL0g0p1XyFfn4V5AdVdB0Hb5SdblgbMUgblLoFFKgD6NxYNGJqVvJ4hC8CNdnBOKytFZWhXkHmtK0DcNsLFzfUBYLMEZdsJQ%2BMOv6BrL91tE6eZm%2BhAq6tXjaLoXdrACEbA9HzQuVZVW0uEgXoWhg%2BOC2iU%2B180dmLKQNTOa%2FmWc4w16tM5xBRgcJeVtw0dO3k0lktsAw3GbR%2BmSmZmW7pFppTgz22NW9DGt1bKzZb765S1EXYx1ev4%2Bdo1pK632tknLwRdT25uzC5J24AFCJPPe34o84Bv2PJAm%2B2SWrpn%2BCkyjrPoH1BAU006MpARE33ae5sngZvHB0kTYWF7CQzyBHUVZsdSXgg6G%2FEN7LZIzDiEbB%2B0234UZbSxt8iaFUNRCEy5chYD5kEuqVs%2BRC7cH8pNQLHthc9hBQmMDBVO1FMWPOdRo9KgIwvsLH2c2t1q3QuISeN5L5S4pqzVk28YiBJuefqMHqj8i3uQcuy4fTtK7OLzTqKApeZJAKPcGUffhgNqJfHTKVYTpa0XmcSU8jeKiS38I48iBRM4Vs6VoLRvkcS%2Bg1O5MC55tKoqEnzs6%2BnMen55FzoemRVC6s4M%2Fx40FNyLVd9W01jpvshThT90hzDTD9jLZlD3caOkUjuyfA%2FrmTiVh%2F3epfEw9Fg10NUIzopfxXAqVDsZlX%2BdbRHc5OjAq6F8h4rUb2xNuFEg%2Be4MPW%2F%2BqZroCva0UcrsCNI2e1zHxTIR%2FNy2sEfL0t1zFQYZP8Lb7ik99tNhBNXYWN9ioUE7NS3%2FgZ7fQafzSBdoGSXqh1sum2zNwqQDN5I16WTmOnLy7YyC2sYBznBXa3sjDmmGdmD7MLjWDOtVnZ6M4ijvFvKKXka4crcm1AF1zAg4r6mt1OQpg
then from there to a destination that depends on the browser’s user-agent.
If the browser’s user-agent is set to a Mac browser, the browser is taken to
update4soft (dot) hugetoupdatecentralreal (dot) work/san?b9zd1=ULKewl34Z_iGnbTwsZHd1fHOfjTuogdKsHUhAlll0gY.&cid=1a669fee-9a44-4724-a33b-2b2f45af8f3c&sub=l93450
The network also checks the browser referer string. If the referer header is blank or is anything except one of the redirectors in the malware network, the user is redirected to Avast.
If the referer string passes the check, the site tries to download Mac malware.
If the browser’s user-agent is set to Mozilla on Windows Chrome on Windows, or Internet Explorer on Windows, the browser is taken to
play (dot) google (dot) com/store/apps/details?id=com.zhiliaoapp.musically&hl=en&gl=US
which is, rather curiously, the TikTok for Android app download.
This I found especially curious; I rarely see a network this extensive that is dedicated solely to Mac malware. So I ran the experiment again from an actual Windows install in a disposable VM to see what would happen.
I used a Windows 10 VM with Chrome, both updated with all current security patches. The behavior from Windows was completely different from the behavior of a Mac browser with a Windows user-agent.
On Windows, clicking the links also redirects to other sites about 10% of the time. Specifically, a true Windows browser redirects to
https://a (dot) bestfaustcaptcha (dot) top/robot4_arrow/index.html?c=097e1524-18d1-49e0-8b6b-df5395fc1c2c&a=l93450#
and from there to
https://joxvvz (dot) hitrichyet (dot) top/ahjtcjqo/?u=3w8p605&o=pn1kfzq&f=1&sid=t4~n30t4f5zeiw2ycgghnozpex2&fp=del%2BGRFgNiQnkzKoWXEUE%2B6ygxzMYSJxsWuPCWbbjDCddCaTtJLx5UOQoqu10Wf9pAN5VKfePiV7uNsCzo9Cao3PynDgMKBX1AZeQT6xeq35s4vE98Ihfwmj2gGdDHxKuQ6x3nh%2FDvAW72ql1fQP81yUjI6Ydnc2XDRoC7XGMEMQcJZTEOjIOUzD%2FUPgUtDiXFwKVZGcX8fwMplib2Q5X0G6QCdbhEk9PT4jFCSphkDFO9NFFOVQSuVCL0aKP%2FSoGGopkQfs4MNoThiPUcIv%2F1pIBHzTCjBR5MhIY0aVaPIaF4PvhQnsaO%2BZgPbrESV4Izo7AgBXnHbpiKD4Dv8Ok%2F0VmgJSVS2Sy0x9vTRxejcPbf293S%2F%2F6GfZor5nz0S%2BYKltZpmbvZtYyJI2mP7AyZ6nXA2n9fs2VAQm1ZXsX0D3HW%2FCaAfUKMIryuz%2BOUVFYzRU8gqsr9N16QBxuZ4wMj8Hj746FT%2FOkW99BtFcU287zRyXCIKQdvM3BG4vEjCCkL1xIy0pm3lFaJSP00KHjSNHqRB0%2FEJf4Fuuk8LyQtYRSi7%2BPtvswGXMrkuWJjvIcV%2Fpuz74vU6nQiYdPD%2BCN9KFlNhD1IMPnVPfK7zwRYKbRF762bWv9qhaQkoc6wcKGtXJyqSwekEs3gbq5NY5cJJr4pNNUlkbLIEY71SpUxTP8%2Bz3gi1sflRVJcowfz%2FwGrJ%2BmhxT2%2FtPP%2Fat1LvwVJLCaHEzqnSXDjU23mjHxvv6nEp1LiKEc0nmSrgeZ9pSB6aqNFWDhmfoFKDNZGegf8rXioCl3fz0VfDIIXnojdZEMpUnoGO1OA3io%2BC50EASNSJtMyoq6nHkUt3HavN2mxZk3%2BmXtsa5wpyf%2BEQah1m7uQoYW6Pe%2FCGyhuAyvTee2eb8Xn9dF%2BB8Vw1LqnE7SnJIcfqZtv6vXzjXLAwOnPUpTYBTzElH9L9WhLqA1uwsYRDWFWdUJGnNm%2FNPxkoxDqYpTFceTldpzpZffTx3VC51O7IbQLtRMKW0R7o%2Ffqt4Xlx8IpaNdhtIkXTjQa14%2FcQiWz3eTRU7eloQqNdKKfDrA87Fm166bZcJuAjypRgbr2NNjiuqirtl%2F1btW37JJ7ENQ0To10jr%2FNGSdWxYhIdHhLf9i9AcYeZVZEfa3JQii7EIT%2Brhbry2pyViEuUmOrOrQkwz6z98lL1INHB6Yc8gXH%2BMK9co9IjRg8Njlp6qafvoMgD8lZDLnH4f77i1q3IMLHee5IVqdhiNC99Rl83nEeaUcrQHE3KR0RVEcYCxX4jEj6xTlrXg9UFIjXLpwSC5TU9rByabs1FZcn%2FrF0CwEQ1J17WDRPM7BXn2wqHC7YO13gbLybFv7E2rhAlo%2FNk4lszYnTM6hza6z0E9jhEmpsKpwLtcDcMgApChvRYvL%2FXOBOV1RR9wl%2BGr%2FCDyJ%2FpfKwa6Ilfku507FS4379tMn5Ip2KzhViUiRd2bQkVYhrgl6nDl0QkwwR%2BtJqKatQmPyMvR9Ex9GWE58GBJEnHWAuZplJxBwIL3q%2FNyRdq4ocUFwCiCo9xcUnYgWA6GYTxWzsvyX5H47yRjU15tf58axudmB3De4JQJ8q2lRZqjqWKambczchthrss9ulFFoyuMfXoFA0oRJ%2B3wbUG3oKS%2BTZdKN%2BUzXv6AAlX4VeiPcJ24Y%2B61t0wk9Fr1MFA8Ko%2BenAuYMZic1xCBZN0Mly8dsyVRPzbVp73%2FHGM%2BfznzNxgfe9Q1F9Sj5Pd3Huz4gT4SXcUwbV7MPqXL8w0JsYoEh%2BTaj8ubnI%2BaNVTYAE3JLuTIDcRw0eleqcfMms5KioHEGpqCSltRBBy%2FPKNX7%2Bn8y0Bba6rCd0jQ1yqkaibcEHaTmEILbXILAeNmGZPy9MEdctz8xZ8nsDsxnRVfwMiX217V6RKaBJOOounJSmKoQHG5rJMqRzDktlGEWCoGIqq5yGOBYvRASvzagFnHZRjBxRQD73QYWax7zFi3olzvIPALkUy%2B09Rap0YVVOzehWls10%2FdQYxoybsQcI3pWpfRrEcfwncQJkOnQWwxASOegWtGW4DzTrgZ11xk6vvKQ6Yzc3rxWKtobp9LTOFjHGQ%3D
which prompts to allow browser alerts.
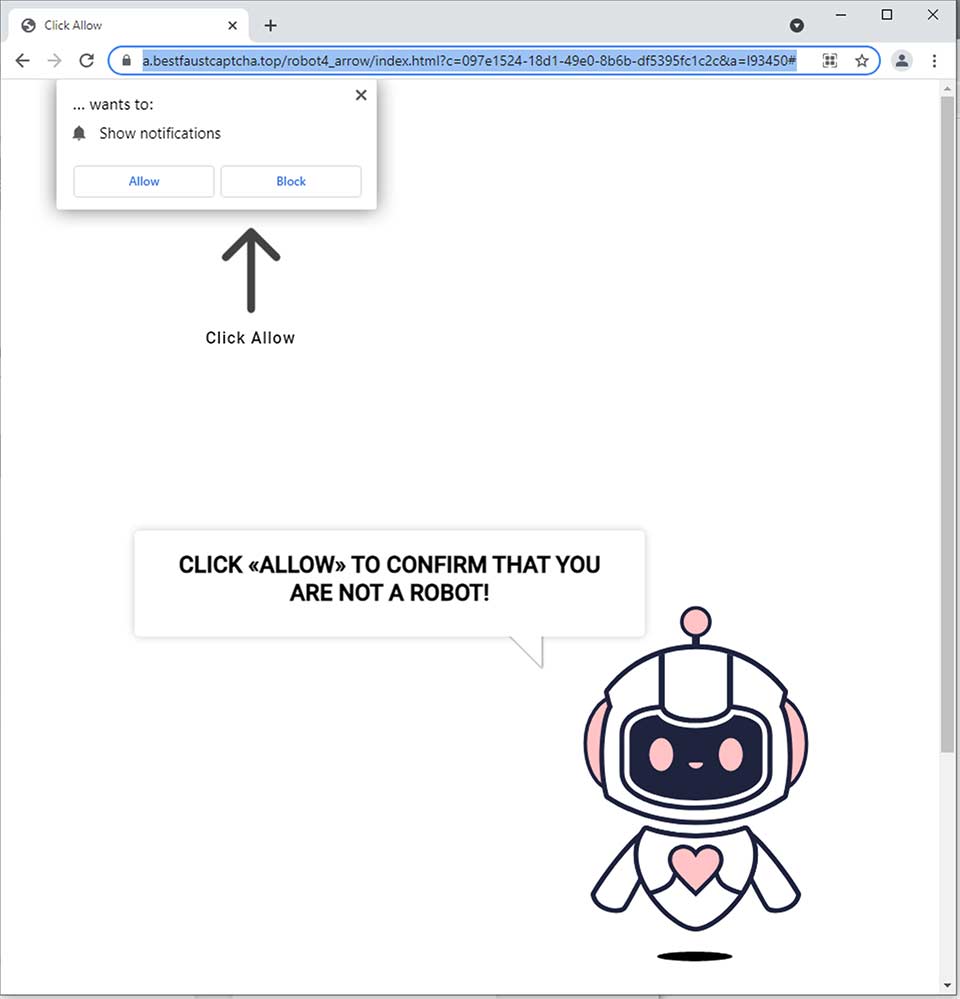
If you choose to allow notifications, you get—surprise!— a fake notification of a phony virus.
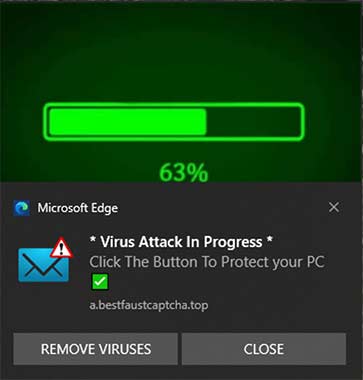
which then redirects via a fake antivirus popup through several intermediaries to
https://rapidlinkmc2 (dot) club/ewCpA/mc/rd23/?isp=CenturyLink&ip=97.115.167.218&g=us&city=Pasco&browser=Chrome&os=Windows&trk=WXpKc05HUklTbkpNYlU1MllsRTlQUT09&tsid=4&lpkey=168043d643b6083316&lng=en&t1=281692&t2=US&uclick=h9twxoh93y&uclickhash=h9twxoh93y-h9twxoh93y-gmb4-0-qd-lpj2-bzd5-448683#
which in turn redirects through several more intermediaries, including
https://followlink (dot) click/nlp/index.php?a=2402&c=43954&s2=d23bch9twxolpi4c58&s4=30&url_bnm_redirect=https%3A%2F%2Fdoneonline.xyz%2Ftohttps://surfshark (dot) com/deals?coupon=surfsharkdeal&transaction_id=1027b5d2a03e441f71613d35fd82bd&offer_id=849&affiliate_id=4912&source=&aff_sub=2402&utm_source=Affiliates&utm_medium=4912&utm_campaign=affiliate&recurring_goal_id=844
which tries to bill about $50 for a VPN subscription.
There’s a lot, and I do mean a lot, of behind-the-scenes examination of the browser referrer, user-agent, machine-specific fingerprinting, and other stuff going on behind the scenes. The machine fingerprinting is especially fascinating; this network is way more sophisticated than other similar malware distributors I’ve seen in the past, that only choose payloads based on user-agent.
Microsoft Edge on Windows behaves the same way.
The network behavior has changed between when I first discovered it three days ago and now. Three days ago, using a Windows user-agent attempted an executable download, which sadly I blocked reflexively. I kinda wish I hadn’t, because I haven’t been able to poke the network into doing that again. I don’t know if it’s doing IP logging or if the network behavior’s been changed.
Also, as of the moment of writing this, Google has cleaned up its search results. Doing the same search that produced all these fake keyword sites no longer does so, meaning someone at Google is on the ball.
The operators of the network are fast to respond. Two days ago, I sent Amazon a notice that Mac malware was being downloaded from an S3 bucket. Yesterday, they disabled it. Today, the Mac malware is being downloaded from a different S3 bucket at
https://s3 (dot) amazonaws (dot) com/67477bf8-74bc-4c1/PpJAkSj/8B303791CC2B19C0B2A94CAC5809C308
I compiled a list of several hundred Web sites stuffed with these keywords. Each one contains 20 links to other such pages. I copy-pasted each of those 20 links, then chose one at random and visited it, then copy-pasted its 20 links, then chose one at random, then copy-pasted its 20 links. I did this a total of 16 times, and put together a text file with 16 pages times 20 links per page = 320 keyword-stuffed pages.
You can download the text file here.
Note that some of the domains are in Cyrillic, so if you see some garbage, keep in mind this textfile’s encoding is Unicode (UTF-8) with Unix line endings.
Some domains appear more than once. I believe these links to be randomly generated. Someone with better math skills than mine can probably look at this file and use Bayesian analysis to make a guess as to how many Web sites are in the network; my gut says thousands.
So what are these sites?
A lot of them are WordPress sites running insecure or outdated WordPress installs. I use WordPress myself, but man, it is a blight on the Internet and a menace to Network security. (If you’re reading this and you run WordPress, please, at a minimum, turn on automatic updates everywhere and install WordFence!)
When I first started looking at this network, I reported the sites as I found them to the Web host’s abuse reporting addresses. I’ve since stopped doing that because there are so many. A lot of the sites I saw (about 20% or so) were hosted on Hostgator, making me afraid that Hostgator had suffered a breach of some kind, though I now believe that was a statistical artifact.
Not all the sites are WordPress. Some simply appear to be poorly secured with weak FTP or Web front-end passwords.
This should, I hope, drive home an important point: Just because your Web site is obscure and gets no traffic doesn’t mean you don’t have to worry about security! These site compromises were done with automated tools, and any site, large or small, can be corralled into a network that can be used for ill. Use strong passwords. Secure your sites. Yes, you.

My problem with one host was that nothing I did could stop my site being infested with php-based malware. I changed passwords, disabled php several different ways (my site is static HTML), disabled FTP and even SSH, complained to management, and still the host correctly complained that malicious php files kept appearing on my site.
The eventual solution was changing hosting companies.
Hi. I have a Mac.
Clicked on a link that came up in a search which had a real adadress. I arrived at this page
hxxps://testpconly12 (dot) coolwayupgradingfree (dot) info/san?b9zd1=ULKewl34Z_iGnbTwsZHd1fHOfjTuogdKsHUhAlll0gY.&cid=5be6ed11-8f60-4fb3-92a7-6a0e179da8cc&sub=l14546
which immediately told me I needed to update my “Flash” and it started to download, or at least, gave me that old Flash updater oval with the blue line filling in rather quickly. I closed the window immediately, but I don’t know if this action prevented anything.
I turned off the WiFi and turned off the computer. When I restarted the computer, it refused my password. I shut the computer down again and started it again. This time, I was able to get back in.
Any recommendations about what to do? Are they able to install malware without me clicking on anything?
Will wiping the entire computer get rid of it?
I took a look. It’s interesting—a fairly standard run of the mill fake “flash player update” site, but with some pretty sophisticated defenses against analysis. It seems to do browser fingerprinting and redirects away from the payload if it sees a browser that’s not vulnerable.
That said, it does look like it needs manual intervention to run the downloaded file, so you’re probably okay.