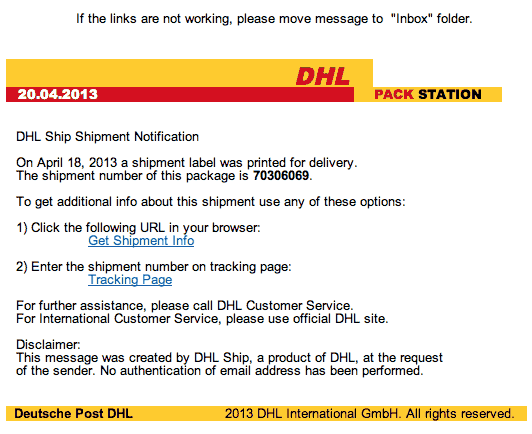
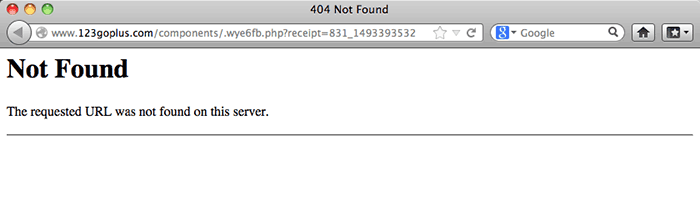
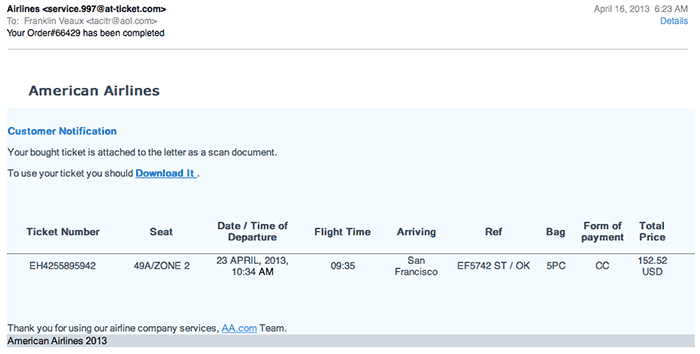
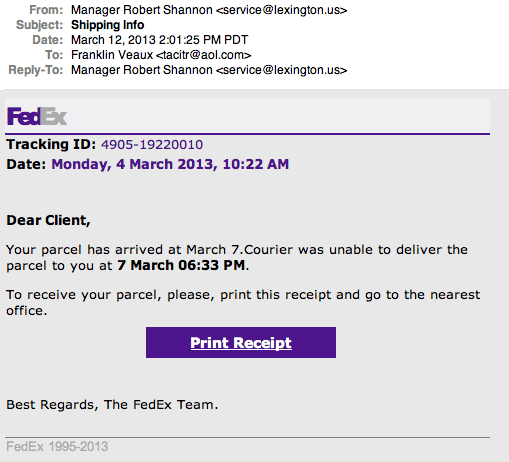
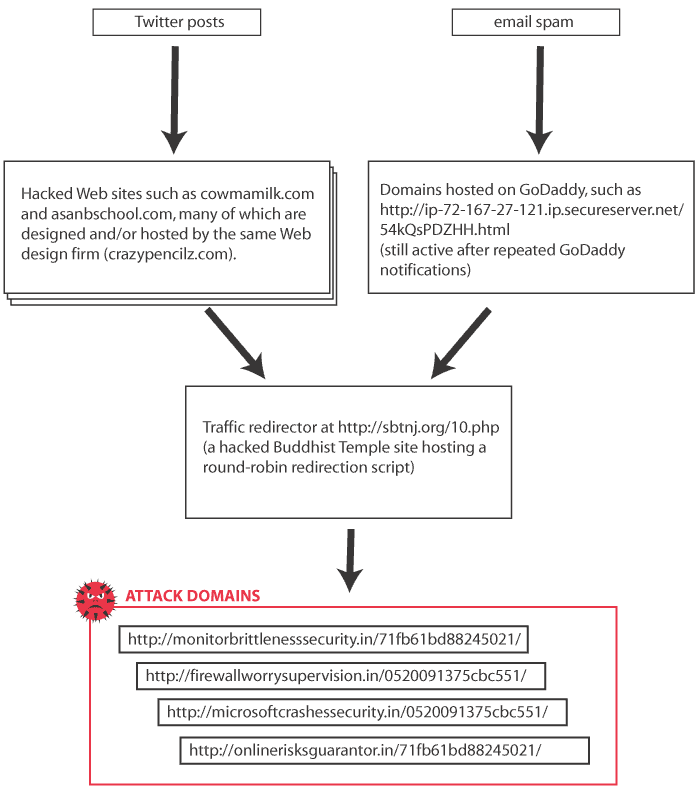
Some time ago, I posted about a malware attack hitting a large number of sites all across the globe, in which hacked Web sites were subverted into distributing a Windows-based bit of malware called W32/Kuluoz, which attempts to steal banking, PayPal, eBay, FTP, and other passwords from your computer.
In that post, I charted the ISPs hosting the most malware-infected sites, and noted that US ISP GoDaddy was, by far, hosting the most active malware droppers.
I used to be a GoDaddy customer. I hosted many Web sites on their servers, some of them for eleven years, and I recommended them to my clients as well. A couple of years back, I started pulling my sites off GoDaddy and recommending that my clients do the same because they began experiencing severe performance issues affecting their shared hosting database servers.
In all the time I have hosted with them in the past, though, the one thing I’ve really liked about them was their abuse team. At the time, it was one of the swiftest, most savvy, most responsive abuse and security teams of any major ISP on the market.
Those days appear to be gone.
The post I linked to above was written in April. Right now, as I type this, many of the malware droppers I saw back then on GoDaddy’s servers are,unbelievably, still active.
GoDaddy, in the spam span of just a couple of years, seems to have gone from being one of the top anti-abuse ISPs to being one of the worst. I have, quite literally, seen tiny ISPs in normally spam and malware friendly havens like Romania deal with security and abuse issues better.
One one level, it might be assumed that large ISPs are just getting worse about security and abuse issues in general. After all, an ISP’s abuse and security team are paid to reduce the company’s revenue, something that’s hard to stomach in a world where hosting providers are becoming part of Wall Street, particularly in an economic downturn.
Or it could be a statistical fluke. As ISPs host more sites, the number of sites with security problems might naturally be expected to increase.
But neither of those ideas seems to explain GoDaddy’s problems. Other ISPs, even large ISPs which have in the past had serious issues with security (like Dreamhost, a hosting company which has in the past had serious security problems of its own), are actually getting better–more responsive, more secure, faster to take down malware-infected sites.
Nearly all the ISPs I have seen be targeted by the Kuluoz malware attacks have grown better at detecting them and better at shutting down compromised sites quickly.
Nearly all, that is, except GoDaddy.
It’s hard to say what’s happening inside GoDaddy. What’s happening from the outside, however, is plain. Its abuse team does not respond to malware and security reports. Reported malware sites stay active for months. There’s a site I first reported to GoDaddy in November that was only finally fixed in May, and I’m not sure it was GoDaddy’s doing; the site owner may have secured the site himself. Repeated complaints to GoDaddy’s abuse team, in email and using their abuse Web form, produce few or no results.
Meanwhile, the entire Internet suffers. GoDaddy customers have their sites compromised and taken over by organized crime. Web surfers get directed to malware droppers hosted by GoDaddy. GoDaddy appears to be aware of the situation, at least if they monitor their Web forms and abuse address (something which has not been conclusively demonstrated, I’ll admit), and chooses not to act.
For a short time, GoDaddy’s Twitter team was responsive to these problems. When I started tweeting about GoDaddy-hosted malware droppers which had been active on their servers for months, I would receive responses like this:
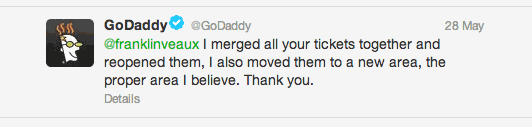
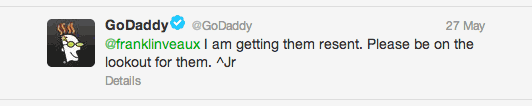
I was briefly hopeful, but the infected sites remained active, still spreadingthe Kuluoz malware.
It’s hard to understand why, as many ISPs move in the direction of being responsive and security-conscious, GoDaddy is moving in the opposite direction.
At the moment, as I type this blog post, I am aware of at many malware droppers on GoDaddy’s servers, many of which have been active for four months or more, including malware droppers on sites like
At this point, it appears the best course of action is to avoid GoDaddy and to advise others to do the same. I no longer recommend GoDaddy to my clients, and I’ve pulled my own sites off their servers. I am also transferring my domains away from GoDaddy as they come up for renewal.
It’s disappointing to see a large company that was once so responsive to abuse and security issues sink to the point where they’re now worse in that regard than ISPs in Romania and Kazakhstan.
There is a saying in the anti-spam community: the normal course of business of a spam-supporting ISP is to go out of business. It will be interesting to see if GoDaddy follows this course, or if they are able to change direction before their inability to act against compromised sites costs them significantly.
UPDATE: Two days after posting this, I received the following email from GoDaddy:
Dear Franklin
Thank you for sharing your feedback with us.
Please rest assured that GoDaddy takes security and malware issues seriously. We have fully investigated your concerns and at this time all reported malware has been removed. We encourage CMS users to follow best practices, keeping core and secondary components such as plug-ins and extensions up to date. We welcome any additional feedback you wish to share in reply.
Thank you for your time and as always, thank you for being a GoDaddy customer.
John M.
Office of the CEO, GoDaddy
14455. N. Hayden Rd. Suite 226
Scottsdale, AZ 85260
CEOTeam@GoDaddy.com
480-505-8828
I’ve checked the emails I’ve sent them, and sure enough, all the malware droppers are gone.