As regular readers of this blog know, I am an amateur infosec researcher, and I track spam and malware as a hobby. And, as many of you know, there are certain names–ISPs, people, affiliate networks, content delivery networks–that tend to come up again and again whenever you do a deep dive into the seedy, twisted world of spam and malware.
A while back, I wrote a blog post about a prolific spammer named Mike Boehm, who makes money sending spam emails that advertise affiliate links on affiliate Web sites. Every time someone clicks a link in one of his spam emails, they’re redirected through a network of computers, all designed to put distance between the spam email and the final site, until eventually arriving at an affiliate Web site, which pays Mr. Boehm for the referral.
Lately, I’ve found myself buried under a blizzard–nay, dare I say, a tsunami–of spam emails that all have very similar characteristics. They advertise a site, usually with a cheap top level domain that nobody wants such as .stream or .science or .faith. Visiting the site shows a plain white page with an animated “Loading” graphic. Then, after a few seconds, you end up on a completely different site, the one actually advertised in the spam.
These spam emails have some but not all of the characteristics of Mike Boehm spam. It’s been hard to track them, because they use complex JavaScript to attempt to hide how the redirection works, what affiliate network they’re using, and where they redirect to. I’ve been collecting examples, and as the number of these spam emails arriving in my inbox has risen, so too has my blood pressure.
Today, it finally reached the point where I sat down and did the work to take apart the tricky JavaScript redirectors and figure out what’s happening.
Lo and behold, the JavaScript is used to redirect visitors through Clickbank, a favored affiliate network used by Mike Boehm in the past.
The system works like this:
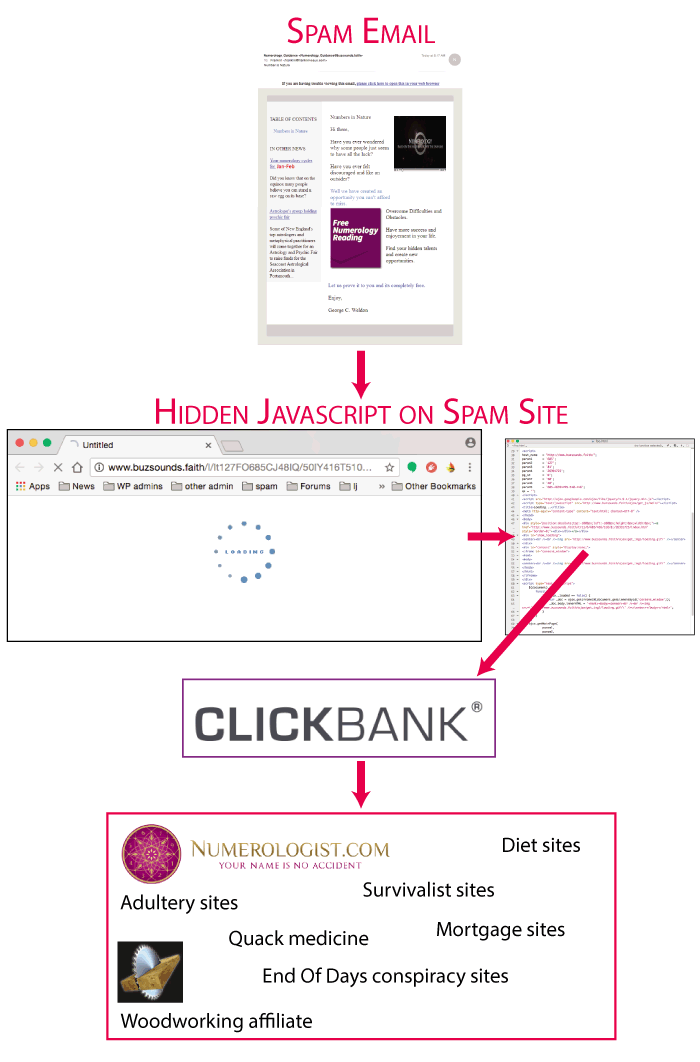
Basically, the spamvertised site contains hidden iFrames and/or hidden divs that have a redirection JavaScript. The redirection JavaScript attempts to conceal where the page is redirecting to. The code on the Spamvertised pages looks like this:
<title>Loading…</title>
<meta hxxp-equiv=”content-type” content=”text/html; charset=UTF-8″ />
</head>
<body>
<div style=”position:absolute;top:-1000px;left:-1000px;height:0px;width:0px;”><a href=”hxxp://www.buzsounds.faith/tr11/6/685/416/510/81/26391725/index.htm” style=”border=0;”><div></div></a></div>
<div id=”show_loading”>
<center><br /><br /><img src=’hxxp://[spamvertised domain]/ajax/get_imgl/loading.gif/’ /></center>
</div>
<div id=”content” style=”display:none;”>
<iframe id=”content_window”>
<html>
<body>
<center><br /><br /><img src=’hxxp://[spamvertised domain]/ajax/get_imgl/loading.gif/’ /></center>
</body>
</html>
</iframe>
</div>
<script type=”text/javascript”>
$(document).ready(
function() {
if (ajax._loaded == false) {
var _doc = ajax.getIframeCW(document.getElementById(‘content_window’));
_doc.body.innerHTML = ‘<html><body><center><br /><br /><img src=\’hxxp://[spamvertised domain]/ajax/get_imgl/loading.gif/\’ /></center></body></html>’;
}
}
);
ajax.getMainPage(
param1,
param2,
param3,
param4,
param5,
param6,
param7,
qs
);
</script>
The JavaScript loaded from the script tag assembles a URL from the parameters, then loads the content of that URL.
var _u = “”;
if (u == ”) {
if (o == ” && c == ”) {
_u = host_name+’ajax_m/get_main_page/’+m+’/’+l+’/’+li+’/’+s+’/’;
}else{
_u = host_name+’ajax_m/get_main_page/’+m+’/’+l+’/’+li+’/’+s+’/’+o+’/’+c+’/’;
}
}else {
if (o == ” && c == ”) {
_u = host_name+’ajax_m/get_main_page/’+m+’/’+l+’/’+li+’/’+s+’/’+u+’/’;
}else{
_u = host_name+’ajax_m/get_main_page/’+m+’/’+l+’/’+li+’/’+s+’/’+u+’/’+o+’/’+c+’/’;
}
}
if(qs != ”) {
_u = _u+”qs/?”+qs;
}
$.ajax({
url: _u,
success: function(data) {
if (pg_st == 0) {
var _w = window;
_w.location = data;
}else{
$(‘#show_loading’).css(‘display’,’block’);
$(‘#content’).css(‘display’,’none’);
var _doc = document.getElementById(‘content_window’);
_doc.src = data;
_doc.onload = ajax.flip;
}
}
});
},
The URL that’s assembled contains nothing but a text string to yet another URL. And, as it turns out, that URL belongs–surprise!–to Clickbank.
In the past, Clickbank has been reasonably responsive to spam complaints. I won’t say they’re great (they’re slow and often don’t take action until I’ve complained multiple times), but they do eventually shut down spamming affiliates.
They shut Mike Boehm down multiple times, and for a while, I was seeing very little spam from him.
This new tsunami of spam, accompanied by the sneaky attempts to conceal the Clickbank redirects, suggests that he’s back to his old tricks, but this time trying to prevent anyone from complaining and having him shut down again.
I’ve managed to find the affiliate IDs he’s using and file complaints with Clickbank. I hope they shut him down again.
There’s a degree of entitlement among spammers I rarely see outside abusers.
