…or, why do I get all this spam, and who’s serving it?
Spammers have long had to face a problem. Legitimate Web hosting companies don’t host spam sites. Almost all Web hosts have policies against spam, so spammers have to figure out how to get their sites hosted. After all, if you can’t go to the spammer’s website to buy something, the spammer can’t make money, right?
In the past, spammers have used overseas Web hosting companies, in countries like China or Romania, that are willing to turn a blind eye to spam in exchange for money. A lot of spammers still do this, but it’s becoming less common, as even these countries have become increasingly reluctant to host spam sites.
For a while, many spammers were turning to hacked websites. Someone would set up a WordPress blog or a Joomla site but wouldn’t keep on top of security patches. The spammers would use automated tools capable of scanning hundreds of thousands of sites looking for vulnerabilities and hacking them automatically, then they’d place the spam pages on the hacked site. And a lot of spammers still do this.
But increasingly, spammers are turning to the new big thing in bulletproof spam serving: content delivery networks like Cloudflare.
What is a content delivery network?
Basically, a content delivery network is a bunch of servers that sit between a traditional Web server and you, the Web user.
A ‘normal’ Web server arrangement looks something like this:
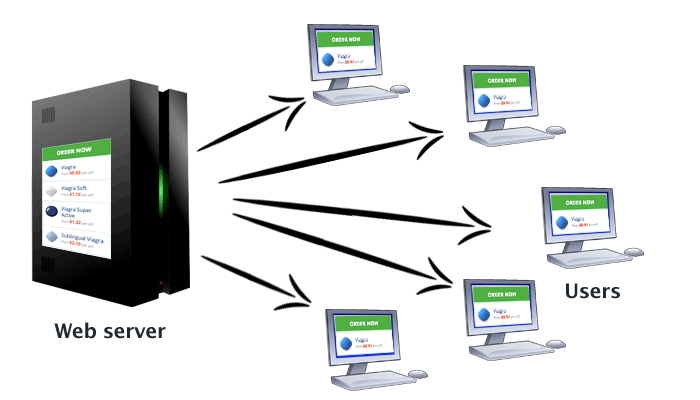
When you browse the Web, you connect directly to a Web server over the Internet. The Web server takes the information stored on it and sends it to your computer.
With a content delivery network, it looks more like this:
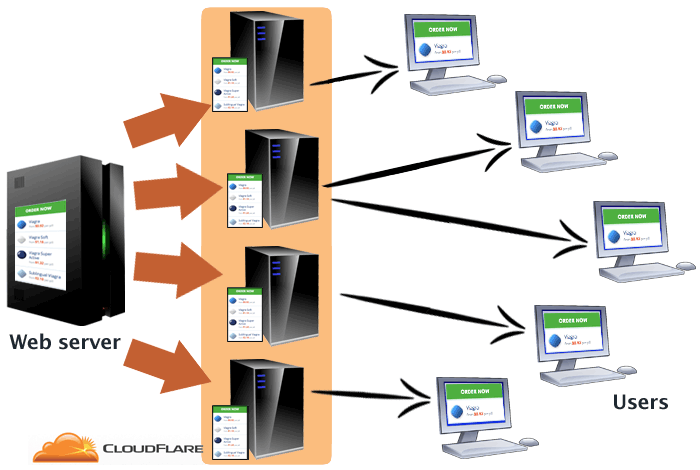
The CDN, like Cloudflare, has a large number of servers, often spread all over the country (or the globe). These servers make a copy of the information on the Web server. When you visit a website served by a CDN, you do not connect to the Web server. You connect to one of the content delivery network servers, which sends you the copy of the information it made from the Web server.
There are several advantages to doing this:
1. The Web server can handle more traffic. With a conventional Web server, if too many people visit the Web site at the same time, the Web server can’t handle the traffic, and it goes down.
2. The site is protected from hacking and denial-of-service attacks. If someone tries to hack the site or knock it offline, at most they can affect one of the CDN servers. The others keep going.
3. It’s faster. If you are in Los Angeles and the Web server is in New York, the information has to travel many “hops” through the Internet to reach you. If you’re in Los Angeles and the content delivery network has a server in Los Angeles, you’ll connect to it. There are fewer hops for the information to pass through, so it’s delivered more quickly.
Cloudflare and spam
Spammers love Cloudflare for two reasons. First, when a Web server is behind Cloudflare’s network, it is in many ways hidden from view. You can’t tell who’s hosting it just by looking at its IP address, the way you can with a conventional Web server, because the IP address you see is for Cloudflare, not the host.
Second, Cloudflare is fine with spam. They’re happy to provide content delivery services for spam, malware, “phish” sites like phony bank or PayPal sites–basically, whatever you want.
Cloudflare’s Web page says, a little defensively, “CloudFlare is a pass-through network provider that automatically caches content for a limited period in order to improve network performance. CloudFlare is not a hosting provider and does not provide hosting services for any website. We do not have the capability to remove content from the web.” And, technically speaking, that’s true.
Cloudflare doesn’t own the Web server. They don’t control what’s on it and they can’t take it offline. So, from a literal, technical perspective, they’re right when they say they can’t remove content from the web.
They can, however, refuse to provide services for spammers. They can do that, but they don’t.
History
CloudFlare was founded by Matthew Prince, Lee Holloway, and Michelle Zatlyn, three people who had previously worked on Project Honey Pot, which was–ironically–an anti-spam, anti-malware project.
Project Honey Pot allows website owners to track spam and hack attacks against their websites and block malicious traffic. In an interview with Forbes magazine, Michelle Zatlyn said:
“I didn’t know a lot about website security, but Matthew told me about Project Honey Pot and said that 80,000 websites had signed up around the world. And I thought ‘That’s a lot of people.’ They had no budget. You sign up and you get nothing. You just track the bad guys. You don’t get protection from them. And I just didn’t understand why so many people had signed up.”
It was then that Prince suggested creating a service to protect websites and stop spammers. “That’s something I could be proud of,’” Zatlyn says. “And so that’s how it started.”
So Cloudflare, which was founded with the goal of stopping spammers by three anti-spam activists, is now a one-stop, bulletproof supplier for spam and malware services.
The problem
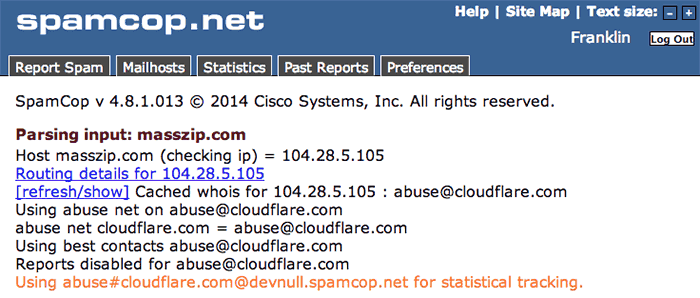
Cloudflare, either intentionally or deliberately, has a broken internal process for dealing with spam and abuse complaints. Spamcop–a large anti-spam website that processes spam emails, tracks the responsible mail and Web hosts and notifies them of the spam–will no longer communicate with Cloudflare, because Cloudflare does not pay attention to email reports of abuse even though it has a dedicated abuse email address (that’s often unworkakble, as Cloudflare has in the past enabled spam filtering on that address, meaning spam complaints get deleted as spam).
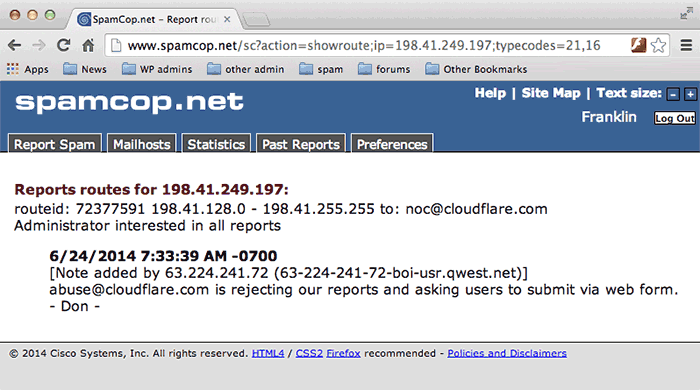
Large numbers of organized spam gangs sign up for Cloudflare services. I track all the spam that comes into my mailbox, and I see so much spam that’s served by Cloudflare I keep a special mailbox for it.
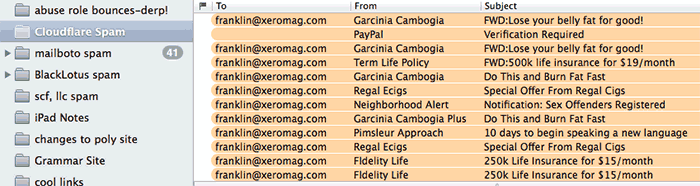
Right now, about 15% of all the spam I receive is protected by Cloudflare. Repeated complaints to their abuse team, either to their abuse email addres or on their abuse Web form, generally have no effect. As I’ve documented here, Cloudflare will continue to provide services for spam, malware, and phish sites even long after the Web host that’s responsible for them has taken them down; they kept providing services for the malware domain
One of the spam emails in my Cloudflare inbox dates back to November of 2013. The Spamvertised domain,
@xxdesmus @CloudFlare I've now reported the phish you're serving at your Web site and your abuse address. On April 8. It's still live. #fail
— franklin veaux (@franklinveaux) April 16, 2014
@franklinveaux @CloudFlare we continue not to host websites. The actual host of the domain and the content will need to more it.
— Justin (@xxdesmus) April 16, 2014
@franklinveaux @CloudFlare once we’ve received the report via the form indicated we will put up an interstitial warning, and notify the host
— Justin (@xxdesmus) April 16, 2014
(They never did put up the interstitial warning, and continued to serve the PayPal phish page for another month or more.)
@xxdesmus That's why your CDN is so popular with spammers. You're basically bulletproof spam providers. Unwitting, perhaps. @CloudFlare
— franklin veaux (@franklinveaux) April 16, 2014
@franklinveaux @CloudFlare you're entitled to believe whatever you'd like to.
— Justin (@xxdesmus) April 16, 2014
Cloudflare also continues to provide services for sites like
In fact, I’ve been corresponding with a US copyright attorney about the
I am not sure what happened within Cloudflare to make them so reluctant to terminate their users even in cases of egregious abuse, such as penis-pill spam, piracy, and malware distribution. From everything I can find, it was started by people genuinely dedicated to protecting the Internet from spam and malware, but somehow, somewhere along the way, they dropped the ball.
I wonder if Michelle Zatlyn is still proud.

They also support criminal activity
See: http://www.crimeflare.com/carders.html
They also support criminal activity
See: http://www.crimeflare.com/carders.html
Is there a way for common users to just block content from CloudFlare entirely? If enough people blacklist them, then they’re going to be hit right in the wallet and be forced to start listening again.
Is there a way for common users to just block content from CloudFlare entirely? If enough people blacklist them, then they’re going to be hit right in the wallet and be forced to start listening again.