I get, as most folks do, a lot of spam in my inbox. A lot of spam.
And, as most folks who follow my blog know, I dedicate some time to tracking down that spam, especially when it involves hacked Web sites.
Lately, I’ve been getting a tremendous amount of spam that all looks pretty similar. It usually offers phony lose-weight-quick products, miracle hair regrowers, and other health and beauty scams, and the emails all tend to look pretty much the same. Here’s an example:
Pretty bog-standard stuff.
These emails invariably contain URLs that are either hacked sites or sites that have no content at all on the home page. The hacked sites are straightforward; the spammers hack the site, put in a new subdirectory, and put an index file that redirects to another site. The sites that have no content on their top level are a puzzler; it’s not clear if the spammers are setting up these sites themselves, using fake or stolen credit card information, or are hacking into sites that have been reserved and configured for hosting but have never had any content placed in them.
Where it gets interesting is in what happens after that.
Clicking on the URL in a spam email takes you to the hacked or blank site, and leads to a redirector. The redirector leads to another, and another, and another, and another, until you finally end up at the spam site. The chain of events looks like this:
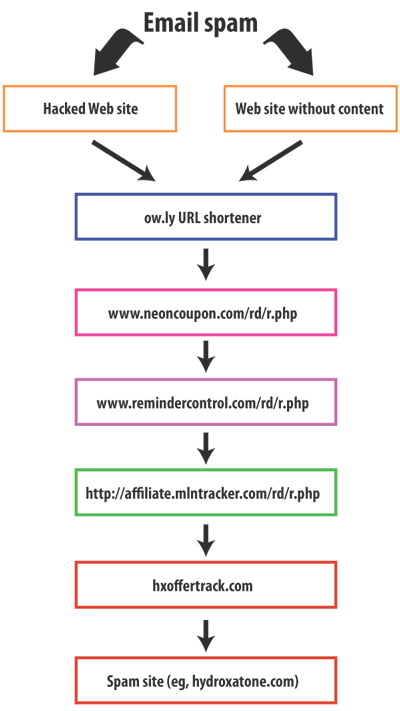
The first stop on the chain is ow.ly, a URL shortener used by Hootsuite, the social media company that lets you manage multiple Twitter, LinkedIn, Facebook, and other social media accounts.
Hootsuite is a large, rapidly-growing company that is filled with bright, ambitious programmers who appear to know very little about security and nothing at all about abuse prevention. I wrote a blog post a while ago with a flowchart of Web 2.0 startups; Hootsuite appears to be somewhere in the early stages of the Loss of Innocence part of the chart, having not yet keyed into the fact that their URL shortener is becoming popular with malware droppers and spammers. (The poor naive dears are still so innocent, they have no mechanism at all for reporting ow.ly spam! I predict that’s going to bite them in the ass in an ugly way, soon.)
After that, things get more interesting.
The ow.ly URL shortener redirects to a site called
Domain Name:
neoncoupon.com
Registrar:Name.com LLCExpiration Date: 2013-09-19 15:44:22
Creation Date: 2012-09-19 15:44:22Name Servers:
ns1.p02.dynect.net
ns2.p02.dynect.net
ns3.p02.dynect.net
ns4.p02.dynect.net REGISTRANT CONTACT INFO
Whois Privacy Protection Service, Inc.
Whois Agent
PMB 368, 14150 NE 20th St – F1
Bellevue
WA
So nothing useful there.
The next stop on the chain,
Domain Name:
remindercontrol.com
Registrar:Name.com LLCExpiration Date: 2014-06-15 16:05:03
Creation Date: 2012-06-15 16:05:03Name Servers:
ns1.p02.dynect.net
ns2.p02.dynect.net
ns3.p02.dynect.net
ns4.p02.dynect.net REGISTRANT CONTACT INFO
Whois Privacy Protection Service, Inc.
Whois Agent
PMB 368, 14150 NE 20th St – F1
Bellevue
WA
So it’s safe to say these two traffic redirection domains (and likely more like them) are probably owned by the same people.
The next stop is interesting. It’s
Their offers apparently including fake get-thin-fast products advertised by spammers and hackers. Hey, if you can get seven-figure incomes, who cares where they come from, right?
From the super-exclusive million-dollar wankers, the next stop on the chain is a site called
The whois for
Domain Name:
HXOFFERTRACK.COM
Registrar:GODADDY.COM , LLCCreated on: 02-Apr-13
Expires on: 02-Apr-14
Last Updated on: 26-Apr-13Registrant:
Domains By Proxy, LLC
DomainsByProxy.com
14747 N Northsight Blvd Suite 111, PMB 309
Scottsdale, Arizona 85260
United States
As per usual, the owner is hidden behind a proxy. And color me unsurprised to see GoDaddy involved in this somehow…
Finally, we get to the spam site itself, in this case
Registered through:
GoDaddy.com , LLC(http://www.godaddy.com)
Domain Name:HYDROXATONE.COM
Created on: 07-Apr-05
Expires on: 07-Apr-14
Last Updated on: 01-Mar-13Registrant:
Domains By Proxy, LLC
DomainsByProxy.com
14747 N Northsight Blvd Suite 111, PMB 309
Scottsdale, Arizona 85260
United States
So to recap: The spammers hack a site, or possibly set up a blank site. They put a redirector on the site which goes through two stages of redirection on sites they probably own, then through a “private affiliate marketing site for seven-figure affiliates” that appears not to care too much about where their affiliate traffic comes from, then through an analytics company, then finally on to the spam site itself.
It has been common practice for a long while for spammers to hack Web sites, install redirectors on them, and point the redirectors to the actual spam Web sites. That way, when people complain about the spam, the hacked Web sites get shut down…but the actual spam sites themselves live on, since nobody can be arsed to follow the chain.
It seems they’re getting savvier, though. I can guess what the “invite-only” seven-figure-affiliate thing is probably all about: a network of spammers, for spammers, by spammers. Traditional organized crime could learn a few lessons about organization from online organized crime!
The addition of analytics to the spam shows a new level of sophistication. Spammers have long been skilled at emotional manipulation; analytics data allows them to fine-tune their pitches, carefully monitoring what kind of spam gets the best results.
