A while ago, I received a spam email. The email came from an obviously hacked attack, and contained nothing but a Web URL.
This usually means either a phony pharmacy spam or a computer virus. Since I am interested in these things, and since I keep virtual machines with redundant backups so I’m not too concerned about malware, I followed it. It lead to a GoDaddy site which redirected to a PHP redirection script living on a hacked Web site which led in turn to a fake antiviurs page–a page that throws up a phony virus “warning” and prompts the mark to download an antivirus program to “fix” the problem. The supposed “antivirus program” is, of course, actually malware. Pretty run-of-the-mill stuff. I reported it to the Web hosts and moved on.
Then, a few days later, I started seeing Twitter posts that were just a URL. These posts led to a hacked site…which led to the same redirector, which then led on to the same malware sites.
Then I started seeing more. And more and more and more. And still more.
I did a Google search. Just one of the hacked sites, an Indian site called
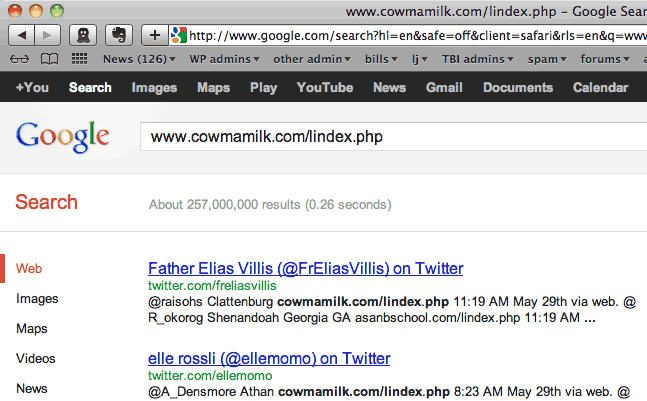
This is a huge scale attack, flooding Twitter with hundreds of millions of mentions of hacked Web sites that in turn redirect to a traffic handler which then sends visitors on to computer malware.
I did some more investigating, mapping out the patterns of redirections, visiting the sites again and again with my browser user agent set in different ways, watching what happened. After a while, I was able to build a map of the attack, which looks something like this:
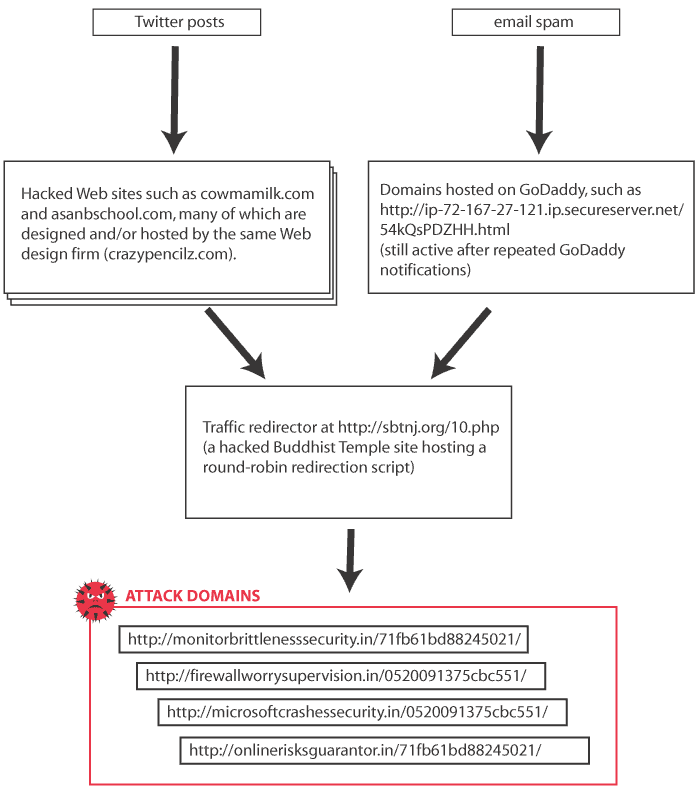
And I found some really interesting things.
I made a list of hacked sites that are being used in the attack by looking at Twitter accounts that were advertising the link to
WARNING *** WARNING *** WARNING
The sites and URLs mentioned in this post are live as of the time of this writing. They do lead to malware sites and they will attempt to infect Windows computers with malware. Do not visit any of these URLs from a Windows machine if you don’t know what you’re doing.
A partial list of hacked attack domains I have put together includes:
And on and on and on. There are lots of these domains. Each of these URLs, according to a Google search, is splattered all over Twitter…hundreds of millions of times, from hundreds of thousands of Twitter accounts that just send out these links over and over and over again.
I looked at the sites, and discovered something very, very interesting: Of all the sites being advertised on Twitter, all the hacked sites that redirect to computer malware, nearly every single one advertises that it was created by the same Web design firm: an outfit called “
Look at the footer of each of the hacked sites and you’ll probably find something like this:
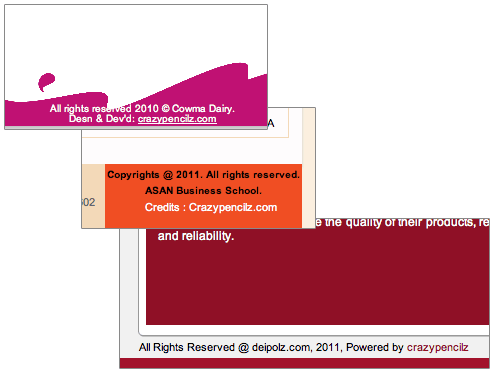
In fact, one of the hacked redirection sites is
So there seems to be one of two likely explanations here. Either
Either way, their Web sites are being hacked and used to host redirectors which redirect to a traffic handling script, also living on a hacked server, which then redirects to many, many malware domains.
The malware domains themselves appear to be living on the same hosting company, an outfit called
When I started writing this post, all the malware sites in the diagram above were live; as of right now, about an hour and a half later, at least two of them are no longer resolving. The Whois information for the malware sites looks like this:
tacit$ whois monitorbrittlenesssecurity.in
Domain ID:D6479050-AFIN
Domain Name:MONITORBRITTLENESSSECURITY.IN
Created On:06-Jun-2012 08:53:19 UTC
Last Updated On:06-Jun-2012 08:53:20 UTC
Expiration Date:06-Jun-2013 08:53:19 UTC
Sponsoring Registrar:Directi Web Services Pvt. Ltd. (R118-AFIN)
Status:CLIENT TRANSFER PROHIBITED
Status:TRANSFER PROHIBITED
Status:ADDPERIOD
Registrant ID:DI_22707501
Registrant Name:Dunstan Puente
Registrant Organization:Dunstan Puente
Registrant Street1:Calle Andalucia 18
Registrant Street2:
Registrant Street3:
Registrant City:Vicar
Registrant State/Province:Almeria
Registrant Postal Code:04738
Registrant Country:ES
Registrant Phone:+34.629138315
Registrant Phone Ext.:
Registrant FAX:
Registrant FAX Ext.:
Registrant Email:nid@lycos.com (the ADMIN and TECH contacts are the same)
Name Server:NS1.DNSEXIT.COM
Name Server:NS2.DNSEXIT.COM
Name Server:NS3.DNSEXIT.COM
Name Server:NS4.DNSEXIT.COM
DNSSEC:Unsigned
So that’s how the network works. Now let’s look at one of the attack domains.
I have been probing the network using wget (to map out the redirectors) and an isolated copy of Safari with various user agent headers (to see how the malware sites work).
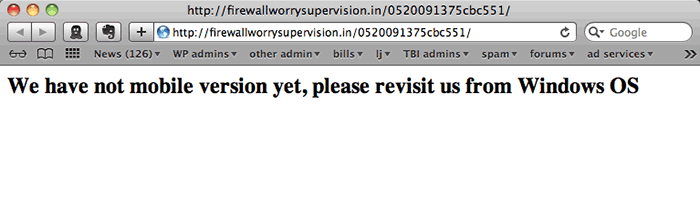
If you visit any of the malware sites using a browser that advertises itself as not being Windows-based, you are presented with a message in broken English, “We have not mobile version yet, please revisit us from Windows OS”:
On the other hand, if your browser user-agent advertises itself as a Windows browser, things are different. First, the site’s window shrinks, and this JavaScript alert pops up.
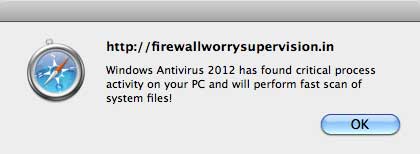
The window then expands to fill the entire screen, and a phony “antivirus scanner” starts to run.
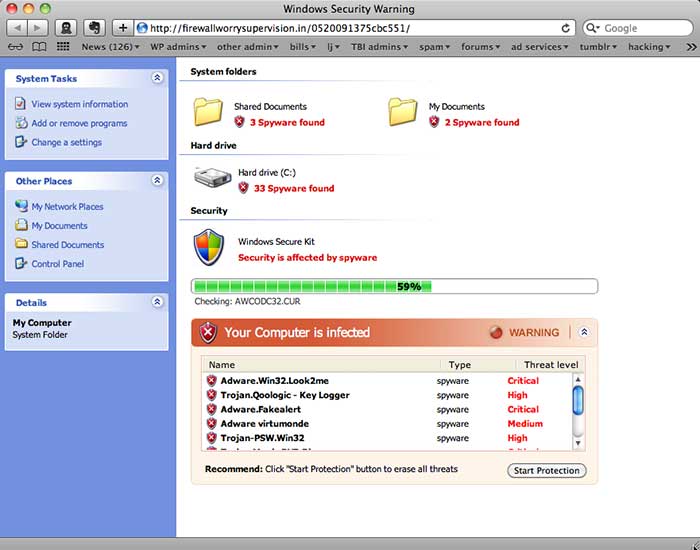
After a few seconds, a fake graphic that is supposed to look like a Windows dialog appears:
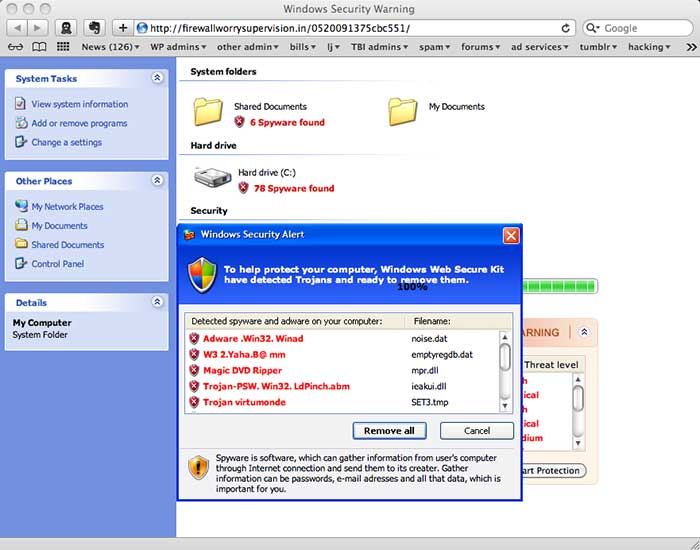
Needless to say, all of this is fake. The graphic in the center isn’t a window, it’s just a picture. At this point, any attempt to click on any part of the browser window triggers the download of a file named “setup.exe” which is, of course, malware.
As of the time of writing this, the file “setup.exe” has a size of 1,955,328 bytes and an MD5 hash of baba090ea62032547fb31c80f9c37fd3.
So to recap:
An Indian Web design outfit called “crazypencilz” appears to either have been hacked and had its client list compromised, or to be a rogue company that uses its clients’ sites as part of a malware spreading network.
Web sites belonging to crazypencilz’s clients are being hacked, and redirectors are being placed on them. The URLs of these redirectors are being broadcast from hundreds of thousands of fake Twitter accounts, hundreds of millions of times, in a Twitter attack whose scope is unlike anything I have ever seen before.
Users who click on these URLs are redirected to a traffic handler Web site. The most common one I’ve seen is hosted on
The traffic handler then redirects to a malware site. The malware sites come and go very rapidly, and the traffic handlers are being updated frequently with new lists of malware sites. The malware sites, located in Turkey, attempt to download a “setup.exe” file which installs malware disguised as phony antivirus software.
I have notified the Web hosts that play into this scheme of the sites, to no effect. The GoDaddy redirector that first tipped me off is still active, after days and repeated emails to GoDaddy. Emails to the hosts of the hacked sites have gone unanswered, as have emails to the host of the redirector site. The malware sites are disappearing quickly, but I can’t tell if that’s because the host is moving against them or the site’s owners are changing the malware attack domains rapidly to try to avoid detection and blocklisting.

Very cool. I’m betting a weak or compromised FTP password. But that’s just a guess. People need to use Ssh/sftp.
K.
Very cool. I’m betting a weak or compromised FTP password. But that’s just a guess. People need to use Ssh/sftp.
K.
Could you possibly upload that file to http://www.virustotal.com website? I can’t find that md5 in their database.
Done. 19 of 42 antivirus packages flag it, as Trojan.Win32.FakeAV or FakeAlert.MC2.Eldorado. Its MD5 should be in the database now.
Could you possibly upload that file to http://www.virustotal.com website? I can’t find that md5 in their database.
Ugh, I feel your pain. I spent some time doing this sort of tracing and reporting as well, a few years ago, but just got overwhelmed by the sheer scope of the deployment networks as well as my own, more pressing life duties.
One of the things that I found to be effective was to e-mail the security departments of some of these networks’ uplink providers (Ones a few hops out on a traceroute, like Level3, GBLX, HE, Qwest, ATT, etc), if I didn’t get a response from the network providing immediate connectivity to the compromised/malicious servers. At least… I think it was effective. A day or two after I sent some of those, I saw some entire networks have their Internet routing blackholed, but never received a formal response, so it’s anyone’s guess if my e-mail had anything to do with it.
Still, keep up the good fight. Someone has to. Heh. 🙂
Ugh, I feel your pain. I spent some time doing this sort of tracing and reporting as well, a few years ago, but just got overwhelmed by the sheer scope of the deployment networks as well as my own, more pressing life duties.
One of the things that I found to be effective was to e-mail the security departments of some of these networks’ uplink providers (Ones a few hops out on a traceroute, like Level3, GBLX, HE, Qwest, ATT, etc), if I didn’t get a response from the network providing immediate connectivity to the compromised/malicious servers. At least… I think it was effective. A day or two after I sent some of those, I saw some entire networks have their Internet routing blackholed, but never received a formal response, so it’s anyone’s guess if my e-mail had anything to do with it.
Still, keep up the good fight. Someone has to. Heh. 🙂
Done. 19 of 42 antivirus packages flag it, as Trojan.Win32.FakeAV or FakeAlert.MC2.Eldorado. Its MD5 should be in the database now.
That’s quite strange that your Android did that (the data roaming.) I’ve had mine for almost three months now, and it does nothing of the sort, ever. It could just be that it’s because your phone was through T-Mobile, mine is through Verizon.
That’s quite strange that your Android did that (the data roaming.) I’ve had mine for almost three months now, and it does nothing of the sort, ever. It could just be that it’s because your phone was through T-Mobile, mine is through Verizon.